Hacker
15 penetration testing interview questions (answered by experts)
Want to stand out in a competitive job market? Use these answers to 15 common pentesting interview questions to impress interviewers (or to gauge an interviewee's knowledge)!

mrb3n,
Jan 02
2024
Table of Contents
- 1. What is penetration testing, and can you explain the difference between vulnerability scanning and pentesting?
- Sample penetration testing report template 👇
- 2. Can you describe the differences between risk analysis and penetration testing?
- 3. Can you describe the different phases of a typical penetration testing engagement?
- 4. What makes a system vulnerable?
- 5. How would you handle sensitive data or information you come across during a penetration test?
- 6. Explain the difference between asymmetric encryption and symmetric encryption?
- 7. How do you stay up-to-date with the latest security vulnerabilities and attack techniques?
- 8. What are the strengths and differences between Windows and Linux for web application testing?
- 9. What are your top 3 must-have tools for an AD-centric pentest and why?
- 10. What types of attacks is the Diffie-Hellman (DH) exchange potentially vulnerable to?
- 11. What is union-based SQL Injection?
- 12. What is privilege escalation and how do you handle it?
- 13. What is XXE and what can it be used for?
- 14. What is data packet sniffing?
- 15. Describe an XSS vulnerability in high-level terms. Ideally, as if you were explaining it to someone with only high-level technical knowledge.
- Preparation is key
In the high-stakes realm of cybersecurity, the role of a penetration tester stands out as both highly coveted and fiercely competitive. Navigating an interview for such a position comes with its own set of challenges.
But fear not. Whether you're a hopeful candidate or a recruiter searching for top-tier talent, we've got you covered.
Our guide to 15 carefully curated penetration testing interview questions, answered by seasoned infosec professionals, is here to help!

1. What is penetration testing, and can you explain the difference between vulnerability scanning and pentesting?
💡Interviewers ask this question to see if the candidate understands what a pentester does and can see the bigger picture of why organizations undergo a pentest.
Answer:
“A penetration test is an organized, targeted, and authorized attack that tests the security posture and defensive capabilities of IT infrastructure.
Normally, there’s a specific agreed-upon time frame that a penetration test will span, rules of engagement, and a clearly defined scope.
In the end, the expected deliverable is a detailed penetration test report that security teams can use to mitigate any vulnerabilities that were discovered.
Sample penetration testing report template 👇

A real-world example of a penetration testing report created by the HTB Academy team. Use it as a template for your next report!
Penetration tests are important because they are a great way to check if your security controls and processes are actually working. Without conducting penetration tests, I believe organizations can have a false sense of security.
A simple comparison I keep in mind is that pentesting is like checking if the door to your home is actually locked and the alarm is armed.
I may think “Did I actually lock my door and arm the alarm?” I can turn around and check by trying to open the door.
A penetration test takes this a step further and emulates a malicious attacker without all the destructive elements.
It makes sure the security controls are doing what they are expected to do. Or even identifies the need for security controls where there are none.
The main focus of a vulnerability assessment is to identify and categorize risk associated with vulnerabilities discovered in IT assets. Typically they are conducted using automated scanning tools like Nessus or OpenVAS.
They are commonly conducted as completely different assessments than penetration tests and do not focus on penetrating further into the network environment through the active use of exploits and attack chaining.
Organizations often have a vulnerability assessment done because they are required to for compliance reasons.
PCI-DSS (Payment Card Industry Data Security Standard) is one example, they require an internal and external vulnerability scan quarterly as outlined on page 23 of the PCI DSS v3.2.1 Quick Reference Guide.
That said, a vulnerability assessment is not as comprehensive as a penetration test.”
Hack The Box content to help you answer this question in an interview:
Related read: Interested in landing a job as a SOC analyst? Brush up on these SOC analyst interview questions!
2. Can you describe the differences between risk analysis and penetration testing?
💡Interviewers may ask this question to uncover any risk analysis experience you have and ensure that you understand the differences between the two.
Answer:
“Both risk analysis and penetration testing are important aspects of cybersecurity and can complement each other well.
A risk analysis is the process of studying all potential threats and faults that could lead to vulnerabilities in software.
It doesn’t require any scanning tools or applications, instead, a risk analysis aims to identify assets, vulnerabilities, threats, and the overall impact on the company if the vulnerability were exploited.
On the other hand, a penetration test is the act of lawfully attacking a system to identify any vulnerabilities. This tests whether existing systems and processes are actually working.
Overall, a risk analysis is more practical, identifying potential risks and impacts. Whereas, a penetration test is more technical, going beneath the surface to uncover vulnerabilities.”
3. Can you describe the different phases of a typical penetration testing engagement?
💡Interviewers typically ask this interview question to see if the candidate understands how a penetration tester typically approaches an engagement.
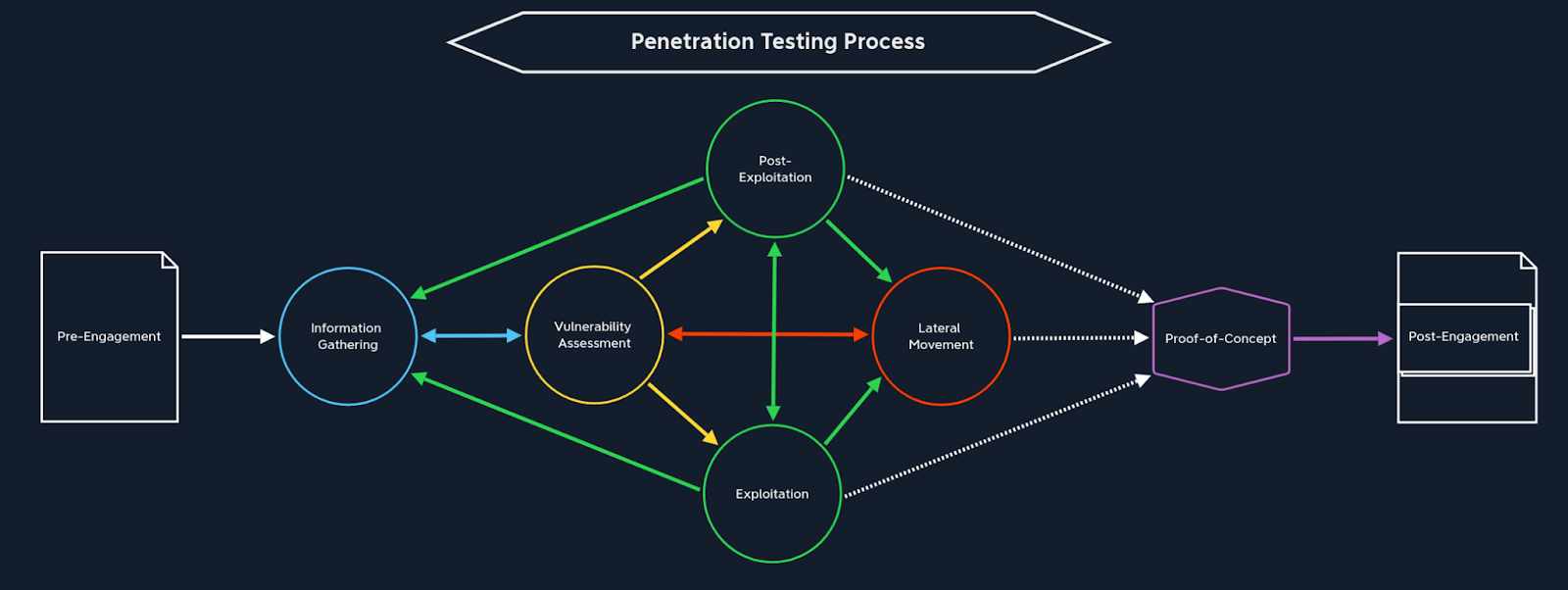
Answer:
“The phases and the order in which they are done can differ depending on who you talk to. In general, these are the phases of a penetration test, many of which will be repeated as the test progresses:
-
Pre-engagement
-
Information gathering
-
Vulnerability assessment (as a phase built-in to the pentest)
-
Exploitation
-
Post-exploitation
-
Lateral movement
-
Post-engagement
During the pre-engagement phase, all of the important work (not as exciting) is done to ensure all relevant parties understand and document the details and expectations of the test.
At the information-gathering phase, the test and fun begins. This is where I start doing open source intelligence (OSINT) and enumerating hosts, the network, and any reachable services.
I will be documenting any promising findings that the client should know about, like:
-
Unexpected services and IP subnets that are reachable.
-
Secrets found in public-facing GitHub repos, AWS S3 buckets, and other cloud storage technologies.
-
Social media activity from employees that may reveal what technologies are used at the company (commonly found on job descriptions).
-
A visual network diagram to assist me in enumeration and discovery throughout the engagement.
At the vulnerability assessment stage, I start using the information we gathered to determine if there are any vulnerabilities present that can be exploited.
I might start looking up known vulnerabilities based on service and software versions, noting any CVEs, finding proof of concept exploits (PoCs), and carefully planning the attack attempts.
At the exploitation phase, I’ll perform the attack and/or series of planned attacks to attempt to exploit any vulnerabilities.
If I have been brought on to test an environment externally and internally, I will be attempting to exploit a vulnerable public-facing system to see if the vulnerability will allow me to pivot from that external-facing system onto internal IT infrastructure.
There are some companies that still host their own websites on-prem in a DMZ, but it is more common for companies to use 3rd party website hosting services or cloud providers for website or web application hosting.
If the engagement calls for me to test from the internal perspective, my contact will provide me with remote access via virtual private network (VPN) or even use an attack VM that gets spun up somewhere on their internal network environment.
Regardless, I will document each attack I attempt (successful and unsuccessful), including the date and time for full transparency.
In the post-exploitation phase, I will check to see what kind of privileges the account I landed on has. If it is a Windows system I’ll run a series of commands to live off the land, discover interesting files, and find potential pathways for privilege escalation, including but not limited to:
-
whoami /priv
-
ipconfig /all
-
netstat -antp
-
arp -a
-
Systeminfo
-
wmic qfe get Caption, Description, HotFixID, InstalledOn
I’ll also look for any interesting files on the system using a series of search-centric commands and scripts (example: WinPEAS) that are configured to look in common directories using keywords that may find files containing sensitive information.
Depending on how secure the environment is, I may choose not to run any type of pre-made scripts to attempt to avoid any potential detections. That said, I understand that it isn’t always bad to get detected as a tester.
It helps the organization see what they are doing right as well, I just wouldn’t want the engagement to end too soon 😊.
At the lateral movement phase, I will use information gathered from what I did in post-exploitation to determine if I can—and how I should—try to move laterally to another system on the network.
Lateral movement and post-exploitation are very closely related, as are all the phases. This may mean that I discover the Windows system I land on is part of a Windows domain, and I try to harvest domain user credentials that I could use to remotely access another system on the network through WinRM.
During the post-engagement phase, the report will be prepped to be delivered to the client. I would, of course, use whatever template our company uses to remain in line with our quality standards, operational practices, and style.
As a team, we may come together to discuss the scoring of each vulnerability to communicate impact and prioritize mitigation based on severity.
We would also work with the client to schedule a time when we can discuss our findings with all the relevant stakeholders.”
Hack The Box content to help you answer this question:
-
All Hack The Box Academy modules in the Penetration Tester Job Role Path

4. What makes a system vulnerable?
💡Assessing vulnerabilities is an important part of pentesting. So interviewers will want to understand your ability to exploit them.
Answer:
“There are various ways a system can be vulnerable, generally falling into the categories of patch management, vulnerability management, and configuration management. Some common examples are as follows:
Running an out-of-date service or application with a known vulnerability that has a public exploit proof-of-concept available.
A misconfigured service or application that can be leveraged to gain unauthorized access (i.e., weak or default credentials, lack permissions, no authentication required, etc.)
A web application that is vulnerable to web application vulnerabilities such as those covered under the OWASP Top 10.
A system that is part of an Active Directory environment that can be accessed via credential reuse or any other myriad of Active Directory attacks.
An end-of-life or unstable system that may be “fragile” and subject to a denial of service condition when stressed.”
Hack The Box can help you answer this question:
5. How would you handle sensitive data or information you come across during a penetration test?
💡Interviewers may ask this pentesting interview question to see if candidates understand the ethical implications and responsibilities that come with being a penetration tester.
Answer:
“Every vulnerability discovered on a client’s network can technically be considered sensitive data or information. Our job as a pentesting team is to help our clients improve security and teach them how they can do so.
As we document our findings, we must be careful and responsible with client data as we’re trusted to do right by them. Suppose we are doing a test for a healthcare provider. It is not my job as a tester to go poking around a database of protected health information (PHI) out of curiosity.
It is my job to discover the vulnerability in the system and understand the impact and potential risk it poses for the client.
Then, document this in a report and deliver it to the client. Some information will be redacted, but we, as a pentesting firm, will likely be keeping a copy of that report on our own company-owned systems.
(We will want to ensure reports are stored on encrypted drives and when moved around over the network, that protocols and message systems use the strongest encryption possible.)
It is also possible that a tester can come across certain information on a system that may be considered illegal content. If this happened to me I would immediately stop the test and consult with my supervisor.
We would likely then communicate the details of what was found and we may even consult with our own legal counsel on how and if we should proceed.”
Need help preparing for interviews?
-
Master complex concepts with free guided cybersecurity courses on the HTB Academy. (Student discounts are available.)
-
Prove that you have job-ready cybersecurity skills by taking the CPTS penetration testing certification (you’ll have example reports and pentests to share in interview assignments).
-
Show your investment in your skills development and earn CPE credits by solving Machines, Challenges, Endgames, and real-world cybersecurity labs.
6. Explain the difference between asymmetric encryption and symmetric encryption?
💡Organizations often use encryption to protect their data, so understanding the difference between the two main types is important.
Answer:
“Symmetric encryption uses a single shared key for both encryption and decryption and is generally faster, requiring less computing resources. It's ideal for bulk data encryption where efficiency is a key consideration.
Asymmetric encryption uses a public and private key pair. The public key is used for encrypting the data, while the private key is used to decrypt (or vice versa). This type of encryption is most commonly used for secure key exchange, digital signatures, and other forms of secure communication.
One practical scenario where both encryption types are in use is when using SSH (Secure Shell) to connect to a server. Asymmetric encryption is used for the initial connection in which a secure key exchange is performed. Symmetric encryption is used for data encryption during the session.
Another scenario is web browsing. Asymmetric encryption is used when first establishing a secure connection to a website via the web browser, while symmetric encryption is used to quickly and efficiently encrypt the data that is transmitted during the browsing session.”
7. How do you stay up-to-date with the latest security vulnerabilities and attack techniques?
💡Interviewers may ask candidates this question to see their continuous learning strategy.
Answer:
“I use a mixture of passive and active learning to stay updated. Of course, I’m on social media sites like LinkedIn, Twitter and YouTube. I’m intentional about following people who post IT and cybersecurity-focused content.
I also subscribe to newsletters like SANs NewsBites. I’ve found this method is faster than waiting on traditional news and media outlets. It is also fun as I may be sitting on the couch or relaxing while learning.
My favorite resources to follow are:
I also like active learning using sites like Hack The Box because this helps me realize the impact and reality of what is mentioned in the news.
The Academy modules and Boxes that get released are often inspired by recent vulnerabilities that have been discovered in the industry.
Exploit CVE-2023-4911 now

- The TwoMillion machine is vulnerable to Looney Tunables, and is available to play on Hack The Box right now.
Often I may come across a post on Twitter that links to a GitHub repo with a PoC exploit for a vulnerability found in Active Directory or something, and I'll try that PoC in my own home lab. I did this with NoPac when it was first announced.
As soon as I saw it work on my lab domain controller, I immediately started notifying my friends and contacts who lead security teams so they could mitigate.”
8. What are the strengths and differences between Windows and Linux for web application testing?
💡Interviewers may ask candidates this question to determine their experience with both systems and their analytical skills.
Answer:
“Windows and Linux both have strengths and weaknesses when it comes to web application testing. For beginners, Windows can be more user-friendly than Linux, which is more challenging to use.
However, Linux is much more reliable and secure in comparison to Windows. This is because inexperienced users often use Windows, making the OS more vulnerable to attackers.
In terms of usability for web application testing, Linux has a wider variety of native penetration testing tools, as well as a high degree of customization. The command-line interface in Linux is ideal for scripting and automation.
Having said this, Windows can be easier to navigate and offers many commercial tools. It’s also important to consider that many organizations use Windows, meaning that pentesting from a Windows machine will much better mimic those real-world scenarios.
I personally advocate for a hybrid approach, upskilling my web application testing using both machines, enabling me to benefit from both.”
HTB content that can help you answer this question:
9. What are your top 3 must-have tools for an AD-centric pentest and why?
💡Interviewers may ask candidates this question to see how well candidates understand Active Directory pentesting.
Answer:
“My top 3 AD-centric tools are:
BloodHound because it is a comprehensive AD enumeration tool that creates a nice visual map to quickly visualize relations between AD objects, domain, trusts, group policies, group permissions, and more. It quite literally helps me see different attack vectors.
PowerShell because it is already built-in to Windows clients and servers. I like to live off the land whenever possible. Most IT admin teams are already using PowerShell for administrative tasks and many of those same tasks can be useful for pentesters during a pentest.
One example of this would be the ActiveDirectory PowerShell module. This allows admins to interact with AD through the PowerShell command line on a Windows host.
If I was able to find my way to an IT admin’s desktop I may just be able to use their system to gain remote access to the domain controller. Especially if they are using the AD PowerShell module in their daily work.
PowerView.ps1 which is part of the PowerSploit project because it has so many useful tools for enumerating AD objects, discovering shares, and even harvesting TGS tickets to attempt a Kerberoasting attack.”
HTB content that can help you answer this question:
10. What types of attacks is the Diffie-Hellman (DH) exchange potentially vulnerable to?
💡Interviewers may ask this question to assess your understanding of the Diffie-Hellman exchange.
Answer:
“The Diffie-Hellman exchange is a method of securely exchanging keys over a public channel. The parties need no prior knowledge of each other to share this secret cryptographic key.
If not implemented and configured correctly, the Diffie-Helmman key exchange can be vulnerable to several types of attacks, the most common being a Man-in-the-Middle (MitM) attack, Logjam attack, brute-force attack, and side-channel attacks.”
11. What is union-based SQL Injection?
💡Interviewers may ask candidates this question to gauge a candidate’s understanding of different types of SQL injection attacks.
Answer:
“The term ‘union’ in Union-based SQL injection refers to the SQL UNION operator, which combines the results of two or more SELECT queries into a single result set.
In a Union-based SQL injection attack, an attacker appends a crafted UNION SELECT statement to the original query to force the application to return additional data that was not intended to be disclosed.
During a penetration test, I would attempt to identify Union-based SQL Injection vulnerabilities by carefully examining how user inputs are handled in the application. I'd look for potential points of entry where untrusted data is used in SQL queries without proper validation or parameterization.”
Hack The Box content to help you answer this question:
12. What is privilege escalation and how do you handle it?
💡Privilege escalation is a crucial phase during any security assessment, meaning interviews may ask you about it.
Answer:
“Privilege escalation is a type of attack that aims to gain unauthorized privileged access into a system.
The goal of privilege escalation after gaining a foothold on a system is to further our access to the level of an administrative user or find some bit of data (such as a password in a script file) that can be used to move laterally within the network.
Privilege escalation always starts with a detailed enumeration of the system we land on, including but not limited to: the operating system type and version, kernel level, running processes, installed services and applications, current user privileges, network traffic sniffing, hunting for sensitive data in various file types (configuration files, scripts, password managers, spreadsheets, etc.”
Hack The Box content to help you answer this question:
13. What is XXE and what can it be used for?
💡Interviewers may ask candidates this cybersecurity interview question to gauge a candidate’s understanding of XML external entity injection attacks.
Answer:
“XXE occurs when an attacker can inject malicious XML data into an application's input fields, which is then processed by the server. When the server parses the XML, it may include external entities defined within the XML data, leading to unintended consequences.
My focus would be to identify and exploit XXE vulnerabilities in web applications to demonstrate their impact and potential risks to the organization.
I would use a combination of manual and automated testing techniques to detect and verify these issues. This includes fuzzing, payload injection, and examining application behavior in response to different XML inputs. A wide range of critical actions and information can be gathered through this kind of attack, including but not limited to:
-
Information Disclosure: Attackers can read files from the server's filesystem by specifying external entities that point to local files. This can reveal sensitive information like passwords, configuration files, or system data.
-
Denial of Service (DoS): Attackers can trigger resource-intensive processing by defining large external entities, causing the server to consume excessive CPU and memory resources and potentially leading to a denial of service.
-
Server-side request forgery (SSRF): Attackers can abuse XXE to make the server perform unintended HTTP requests to internal or external resources, leading to further attacks like scanning internal systems or accessing sensitive APIs.
-
Port scanning: An attacker can use XXE to scan ports of internal systems, potentially identifying other vulnerable services.”
Hack The Box content to help you answer this question:
14. What is data packet sniffing?
💡Interviews may ask this question as data packet sniffing is a common pentesting technique.
Answer:
“Packet sniffing is a technique used to capture and analyze data packets as they are traveling across a network.
The process can be used for diagnostic, monitoring, security (i.e., pentesting)., or malicious purposes.
When performing packet sniffing, the device’s network interface card (NIC) is set to promiscuous mode, which allows it to capture all packets on the network regardless of their destination.
The packet sniffing tool is used to intercept and copy data packets on the same network segment where the device is connected. This can include packets not destined for the device running the sniffing tool.
These packets are then analyzed offline for purposes such as troubleshooting network issues, monitoring network performance, or extracting sensitive information (such as credentials if we are performing a penetration test).
The process may also be used by malicious actors to attempt to intercept sensitive data.
Packet sniffing can be countered by ensuring that secure network protocols and strong encryption are employed across the network. An Intrusion Detection System (IDS) can also be used to alert administrators to malicious packet sniffing activities.”
15. Describe an XSS vulnerability in high-level terms. Ideally, as if you were explaining it to someone with only high-level technical knowledge.
💡Interviewers may ask candidates this question to grasp a candidate's ability to communicate complex technical information in an easy-to-understand manner.
Answer:
“A cross-site scripting (XSS) vulnerability is a type of security issue that occurs when malicious code is injected (e.g., malicious SQL statements) into a website or web application, allowing attackers to execute their code on the browsers of unsuspecting users.
Imagine your website as a house with different rooms for various functionalities. Such as login, messaging, or user profiles.
XSS is like an intruder who finds a way to slip a harmful message or piece of code inside one of these rooms. When an unsuspecting visitor enters that room (opens a specific page or clicks a link), the intruder's code executes in the visitor's browser.
This can have several negative consequences, including but not limited to:
-
Data theft: The attacker can steal sensitive user information, such as login credentials, personal details, or payment card data.
-
Session hijacking: By exploiting XSS, the attacker could hijack an authenticated user's session, gain unauthorized user access to their account, and perform actions on their behalf.
-
Malicious actions: Attackers might use the vulnerability to trick users into unknowingly performing harmful actions, such as changing account settings or making unauthorized transactions.
-
Phishing attacks: XSS can be used to present fake login forms, leading users to believe they are entering their credentials on a legitimate website, but in reality, they are providing the information to the attacker.
To protect against XSS, it's essential to follow secure coding practices, validate and sanitize user input, and implement security mechanisms that restrict the execution of untrusted code on the website.”
Hack The Box content to help you answer this question:
Preparation is key
These are just some of the questions you may come across in a penetration tester interview, but they are by no means set in stone.
So, it’s important to be a lifelong learner and consistently upskill to ensure that you’re up to speed with the latest threats and techniques.
But remember, you aren’t expected to know everything, no one is! It’s impossible to know everything, so don’t pretend to. Be honest if you’re unsure of an answer.
You’ve got this!
At Hack The Box, we’re here to help cybersecurity professionals get hired and recruiters hire the best candidates.
Aspiring hackers can apply directly to roles posted by companies worldwide. This includes roles from organizations like Amazon Web Services, NTT, Verizon, Daimler, DAZN, Context Information Security, and more.
At the same time, recruiters can access a growing pool of talented individuals and look for their next cybersecurity star hire. Our new and revamped Talent Search helps recruiters find the perfect candidate more quickly and confidently than ever.
|
Author bio: Ben Rollin (mrb3n), Head of Information Security, Hack The Box Ben Rollin has over 13 years of information security consulting experience focusing on technical IT Audits, risk assessments, web application security assessments, and network penetration testing against large enterprise environments. He has a strong interest in Active Directory security and focuses time on research in this area as well as remaining current with the latest tactics, techniques, and procedures (TTPs). Ben has a bachelor's degree in Business Administration, as well as several industry certifications including Certified Information Systems Security Professional (CISSP), Certified Information Systems Auditor (CISA), Offensive Security Certified Expert (OSCE), and Offensive Security Certified Professional (OSCP).Feel free to connect with him on LinkedIn. |







