Hacker
How to become an ethical hacker: A step-by-step guide
Our Head of Security, Ben Rollin, calls on more than a decade of experience in cybersecurity to break down the practical steps to a career in ethical hacking.

mrb3n,
Oct 24
2023
Table of Contents
After graduating with a dual bachelor's in Business Administration and Spanish, I worked for a small (less than 20 employees) language translation company. When the designated IT manager was let go, I agreed to pick up his responsibilities and started studying IT, devouring every resource I could get my hands on at the time.
So I basically became a one-man hybrid helpdesk/sysadmin team.
This helped me progress deeper into the world of cybersecurity and into other roles. I eventually performed and led technical security audits and ethical hacking (or penetration testing) at PwC before moving on to a smaller firm.
My journey into cybersecurity isn’t unique. Plenty of people have become ethical hackers later on in their lives without educational or career backgrounds in cybersecurity.
|
In this article, you’ll learn what it really means to be an ethical hacker.
I’ll share my advice on how to get the right training, where to start, and how to know if ethical hacking is a suitable fit for you as a career.
What is ethical hacking?
A textbook definition of “hacking” is the act of finding exploitable weaknesses in computer systems, digital devices, or networks in order to gain unauthorized access to the data they hold.
(If only it were this simple!)
The aim of ethical hackers is to find these weaknesses so that they can be fixed or protected before they are exploited by others.
When ethical hackers are employed by an organization to test computer systems and networks, they are often referred to as “penetration testers.” Organizations use the term when referring to the job description of professional hackers in the corporate world.
White hat hackers is another term used to distinguish between ethical hackers and black hat hackers who work on the other side (the wrong side) of the law.
Grey hat hacker is a term for someone who may be acting for the right reasons but using unethical approaches.
Their intentions may be pure (i.e., bug hunting on a company’s website) but if they are operating outside the bounds of a formal bug bounty program or contract for penetration testing they are still breaking the law.
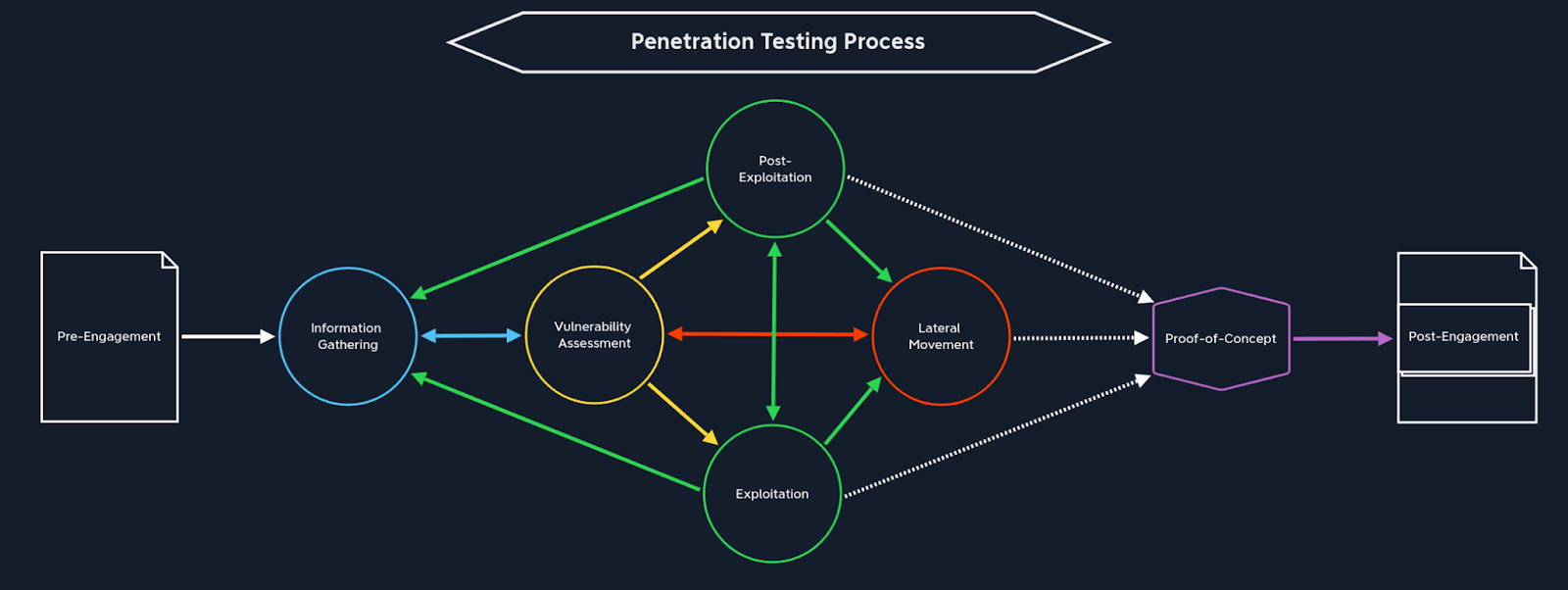
Professional hackers operate under a code of ethics that distinguishes them from non-professional or malicious hackers. The professional cybersecurity organization, (ISC)2, for example, has a code of ethics that has four pillars:
-
Protect society, the common good, necessary public trust and confidence, and the infrastructure.
-
Act honorably, honestly, justly, responsibly, and legally.
-
Provide diligent and competent service to principals.
-
Advance and protect the profession.
All members of (ISC)2 are required to uphold these pillars. These principles are also implied within the discussion of ethical and legal considerations that are covered in the HTB Academy’s module “Penetration Testing Process.”
It covers the approach a penetration tester should take in dealing with a client to stay within the bounds of legal and ethical practice.
Each time you engage in ethical hacking it will be a unique experience that requires out-of-the-box thinking, creativity, and persistence in the face of evolving and unforeseen challenges.
There will be new technologies to understand, that have been configured in unique ways, in a technical landscape that you have to map out.
Become a certified ethical hacker
-
Master complex concepts with free guided cybersecurity courses on the HTB Academy. (Student discounts are available.)
-
Prove that you have job-ready cybersecurity skills by taking the CPTS penetration testing certification (you’ll have example reports and pentests to share in interview assignments).
-
Show your investment in your skills development and earn CPE credits by solving Machines, Challenges, Endgames, and real-world cybersecurity labs.
What does an ethical hacker do?
An ethical hacker’s (or pentester’s) goal is to help uncover and recommend fixes for hidden flaws in digital or physical networks before they are explicitly or accidentally exploited. Companies will ask ethical hackers to do this on specific systems, networks, or infrastructure that will be in scope for testing.
They will then use ethical hacking tools to probe for security vulnerabilities, document processes, and activities, and write penetration testing reports for senior colleagues and the client.
Specific examples of an ethical hacker’s daily activities include:
-
Conducting network/web application vulnerability assessments.
-
Scanning networks with a tool like Nmap.
-
Conducting an analysis of network structure and protocols with a tool like Wireshark.
-
Processing and reviewing large amounts of data or scouring file shares to look for passwords (I’ve spent entire days looking through file shares for login details).
-
Enumerating and attacking Active Directory environments and web applications.
-
Communicating with clients and assisting senior managers and account holders with security debriefs and answering client questions; this could include sales calls or project kick-offs.
-
Documenting findings into a formal report that contains high-level detail for non-technical readers and technical details so those tasked with remediating any findings can reproduce the issue.
Not all of a penetration tester’s time is spent “hacking.” At least 25% of it will be spent writing documentation, liaising with customers, and reporting activities and findings back to internal and external stakeholders.
This is why technical offensive security skills alone are not enough to become an ethical hacker.
You should also have (or consider building) good professional communication and soft skills. This means writing professional emails, being punctual, communicating with non-technical stakeholders, and delivering projects on time.
(A scan of the open ports on a network. Executed on a live practice target via our Academy's in-browser tool, Pwnbox. Click here to try it yourself.)
The traits of an effective ethical hacker

Not everyone is suited to the role of being an ethical hacker. Some of the principal characteristics essential for the role are:
Strong technical skills
There is no single correct path to learn hacking or become an ethical hacker. It is certainly not the case that you need a computer science or cybersecurity university degree to be successful.
Any technical job, certification, or self-study program brings useful knowledge and skills. And once you’re on the job, you can study to fill in specific knowledge gaps.
Will a qualification help get your foot in the door? Sure. But after that, your experience in cybersecurity roles and your ability to network will help you carve out a career path.
Another useful early career booster is a certification of some sort, which we will cover in more detail below.
Prioritize learning methodology, processes, and mindset. Always remember, tools serve art and not the other way around. (Oh, and drink plenty of water!)
Pedro Correia, Redteamer and cybersecurity instructor, Code For All
Persistent and methodical
Being able to stick with a problem until it is resolved and approaching problems in a methodical way is essential in ethical hacking.
Not only for being able to keep at a problem until it is solved but also for performing routine tasks that, to be frank, may be boring and repetitive.
Creative, out-of-the-box thinking
To think out-of-the-box, you first have to know and be able to define what “the box” is.
This goes back to the need for a technical foundation and an understanding of how a range of people involved in the system think and act.
If you understand the assumptions that a developer makes when implementing a protocol or piece of code, you can think out of the box to discover new pathways to attack.
Likewise, if you know how a potential attacker thinks, you can see how they could combine a chain of exploits to get a foothold on a machine, move laterally in a network, and remain undetected.
Real-world penetration testing requires an element of raw human intuition. If human intuition wasn’t needed, then paid software would have solved security by now. This shows that you can’t rely on programmatic or tool-oriented thinking because creativity, adaptability, and out-of-the-box thinking are critical.
Passion for problem-solving
This is where you ask yourself whether you genuinely enjoy problem-solving.
If you have all of the previously mentioned attributes, technical knowledge, persistence, and out-of-the-box creativity, do you enjoy applying them to solve arcane problems that might be just one piece of a 1000-piece puzzle?
Becoming an ethical hacker: 5 key steps
Step 1: Develop your foundational skills for ethical hacking
Beginners should start with the fundamental cybersecurity skills needed for hacking: Networking, Linux, Windows, and scripting.
Regardless of how advanced or basic your exploits become, you’ll always call upon the knowledge and skills related to these core domains.
Mastering these fundamentals will also accelerate your ability to learn more advanced hacking concepts, techniques, and tools.
Get a strong foundation on all major topics of cyber. The broader your knowledge base is, the better you understand complex topics. Learn the basics on guided platforms and try to figure out how you learn best.
Samuel Viegas, Penetration Tester, PwC

Most things in hacking or cybersecurity revolve around a network. This is why a firm grasp of networking and network security fundamentals is foundational for beginner hackers who are learning the ropes.
Understanding how networks are structured and how devices communicate means you can identify, protect, exploit, and of course, remediate weaknesses in networks.
With this knowledge, you’ll know what services are running on a server, what ports and protocols they’re using, and how the traffic behaves.
Recommended read: Learn cybersecurity for free.

An operating system (OS) is software that manages all of the hardware resources associated with a computer. That means that an OS manages the communication between software and hardware.
Learning Linux operating systems is an essential and inevitable step in cybersecurity because Linux covers about two-thirds of the world's servers, including macOS, which is also based on Linux. Linux-based operating systems run on servers, mainframes, desktops, embedded systems such as routers, televisions, video game consoles, and more.

You'll need to understand how to navigate the Windows file system and command line; Windows is still heavily used across corporate environments of all sizes.
During penetration testing engagements, you will often need to gain access to a Windows host. Additionally, many servers run on Windows, and most companies deploy Windows workstations to their employees due to the ease of use for individuals and centralized administration that can be leveraged using Active Directory.
Recommended read: How to become a cybersecurity analyst.

Bash is a command-line interface language used to make instructions and requests to operating systems like Linux. As a hacker, learning how to create bash scripts will help you harness the full power of the Linux OS by automating tasks and enabling you to work with tools.
5. A scripting language (like Python)

Python is a powerful entry-level programming language to learn for cybersecurity because it’s versatile, relatively easy to learn, and plays a key part in compromising systems and networks. You’ll use it to:
-
Automate tasks
-
Write custom scripts
-
Scrape data from the web
-
Analyse packets and data
-
Identify and develop malware
Step 2: Choose your learning path
After building a solid foundation of theoretical knowledge and practical cybersecurity skills, pursue a certification, degree, or self-directed training program that proves your competence in cybersecurity.
Technically, a certification isn’t a strict requirement to becoming an ethical hacker.
But when you start reaching out to recruiters and applying to junior roles, it will tip the odds in your favor by proving your competence and getting your resume past automated screening systems that look for certain requirements, such as a specific certification.
Join the largest hacking community
Ask questions, find a study buddy, get inspired, and level up your hacking career.
Prioritize skills development when deciding which cybersecurity certification to take.
You should also consider:
-
Whether or not the certification prepares you for real-world engagements and penetration tests.
-
The price of the certification, how long you’ll have access to training content, and renewal costs.
-
How well-recognized the certification provider’s brand is amongst recruiters and security professionals.
Call me biased, but I’d recommend Hack The Box’s CPTS certification because it:
1. Focuses on turning you into a complete job-ready penetration tester. To pass the exam, you’ll receive a letter of engagement (just like you would from a real client) and will have to submit a penetration testing report based on your assessment of real-world Active Directory networks hosted on HTB’s infrastructure. This will be reviewed by an examiner (who will also offer personalized feedback on your performance).
2. Emphasizes both practical skills and fundamental knowledge. Combined with the penetration testing job path on the HTB Academy, you’ll have exploited more than 250 realistic targets and attacked 9 various corporate-level networks (ranging from a shipping freight company to a robotics tech company).
This is in stark contrast to other certifications that are CTF-style (somewhat unrealistic) in nature and are primarily based on repeating established common vulnerabilities and exposures (CVEs), and as a result, fail to cultivate the persistence and creativity required for real-world hacking.
3. Offers great value for money. For less than $500/year, you get lifetime access to content that’s continually updated based on the ever-changing cybersecurity landscape (MITRE ATT&CK and NIST aligned), and a certification that prepares you for the real world of pentesting to set you apart from other candidates.
The ultimate pentesting certification
Accelerate your cybersecurity career with the HTB CPTS: The cost-effective, hands-on penetration testing certification that’s valued by employers, prepares you for real-world environments, and gets you job-ready.
Step 3: Prove your practical skills
When I started getting into ethical hacking, there were no affordable hosted lab environments. The main free resources available required you to download a vulnerable machine and hack it, like the Vulnhub platform.
While these were useful to get started, they did not simulate a corporate network. So it was difficult to get experience in a realistic environment (unless you could build a small Active Directory network yourself to experiment with.)
So if you don’t have access already, use hacking labs to simulate practice in real-world corporate environments. Acquiring lab experience is effective for learning and for interviews because it elevates your confidence in your practical skills.
Recommended read: 30 cybersecurity interview questions and answers.
You’ll have the ability to speak authoritatively about things you’ve actually done.
If you had done a certification, you may have gained access to labs to practice the skills required for the exam. Continuing to practice using machines on Hack The Box and other sites is a great way to learn new skills or upskill existing ones.
Watching walkthroughs of machines on YouTube by Ippsec or reading 0xdf’s write-ups is also a great way of learning. Try to constantly read, watch, and complete hacking challenges to refine your craft.
Step 4: Curate your online presence
What does your public profile say about you?
Googling candidates was a common practice when I used to hire professional ethical hackers.
This is general advice when looking for employment, but recruiters commonly look at your online presence when hiring. LinkedIn, GitHub, YouTube, Stack Overflow, and Hack The Box all provide a means of promoting your credentials, achievements, and general standing in the cybersecurity community.
Active steps you can take to stand out include:
Attending hacking events and activities
Play capture the flag events (CTFs) and use hacking labs to show that you’re committed to continuously upskilling and are up to speed on the latest and greatest in cybersecurity. Do you need to play every single CTF or HTB machine?
Of course not. But do enough to show your passion and investment in continuous upskilling.
Note💡: If you’re new to the world of cybersecurity, try HTB seasons. HTB Seasons follows a seasonal scoring model that allows new players to receive recognition, rank, and prizes for showing up-to-date hacking skills and setting new personal records. It’s also a great way to make friends!
You'll make incredible friends in the cybersecurity world. Dive in with confidence! Pursue it wholeheartedly and fall in love with your passion every day.
Jordon M, Network Security, Boeing
Creating content
Create content about the lessons you’ve learned or projects you’ve completed and post them on Medium or your own blog. This could be video content, write-ups, blogs, tutorials, etc.
Step 5: Start applying for jobs
You can find cybersecurity jobs on general sites like LinkedIn or Indeed. But if you’re looking for an extra edge, Hack The Box’s cybersecurity job board is tailor-made to meet the needs of:
-
Recruiters who are searching for candidates with practical skills.
-
Cybersecurity professionals who are looking for jobs.
Once you reach the Pro Hacker rank, Hack The Box can share your public profile with recruiters. This will connect you to jobs and recruiters who value your practical experience.
It’s a great way to accelerate your job search and “show” your skills before you “tell” recruiters about them.
Note💡: If you’re an HTB member, just enable the “Available for Hire” option under the Careers section. Although not mandatory, I’d recommend enabling it because you’ll receive up-to-date opportunities from some of the best companies worldwide.
Recommended resource: Cybersecurity job interview prep: A guide to hacking interviews
Building your career base with IT jobs
Whilst ethical hacking is an exciting and fulfilling career, there are many other related jobs in cybersecurity that have overlapping knowledge and skill sets.
For beginners, it can be difficult to break into pentesting directly (but it’s not impossible). That’s why I wholeheartedly recommend getting as much general IT experience as possible (often with entry-level cybersecurity jobs) before shifting into a highly technical infosec role like ethical hacking.
Frequently Asked Questions about ethical hacking
Can I become an ethical hacker without a degree?
Yes, it is possible, although many people working in the area of cybersecurity have a degree of some sort.
In the 2022 (ISC)2 Cybersecurity Workforce Study, 87% of those responding to the survey said they had at least a bachelor’s degree, and most of these were in a computer science-related subject.
How much do ethical hackers earn?
This depends on what country you are in. In the USA, the average base salary is $119,295. There are sites that will give you an idea of salaries in your country.
How long will the journey take to get into a full-time role?
If you do not count getting a degree which can take between 3 to 4 years for an undergraduate one only, then you should allow 6-12 months to obtain a certification. This would also assume that you were getting practical experience beyond just the certification during that time—i.e., completing labs and machines on HTB, for example.
Stop procrasting. Start your career in cybersecurity.
|
Author bio: Ben Rollin (mrb3n), Head of Information Security, Hack The Box Ben Rollin has over 13 years of information security consulting experience focusing on technical IT Audits, risk assessments, web application security assessments, and network penetration testing against large enterprise environments. He has a strong interest in Active Directory security and focuses time on research in this area as well as remaining current with the latest tactics, techniques, and procedures (TTPs). Ben has a bachelor's degree in Business Administration, as well as several industry certifications including Certified Information Systems Security Professional (CISSP), Certified Information Systems Auditor (CISA), Offensive Security Certified Expert (OSCE), and Offensive Security Certified Professional (OSCP).Feel free to connect with him on LinkedIn. |







