Hacker
30 cybersecurity interview questions and answers (beginner-advanced)
Ace your next cybersecurity interview or identify the right cyber talent with these 30 cybersecurity interview questions and answers (sourced from experienced infosec pros)!

ltnbob,
Oct 17
2023
Table of Contents
- 10 junior cybersecurity interview questions and answers
- 1. What is penetration testing, and can you explain the difference between vulnerability scanning and pentesting?
- 2. Can you describe the different phases of a typical penetration testing engagement?
- 3. How would you handle sensitive data or information you come across during a penetration test?
- 4. How do you stay up-to-date with the latest security vulnerabilities and attack techniques?
- 5. Do you have a home lab? If so, tell me about it.
- 6. What is your rank on HTB or other platforms, and do you prefer to participate in CTFs with a team or by yourself?
- 7. Do you volunteer at security conferences or local infosec meetups?
- 8. What is your favorite Linux distribution and why?
- 9. Explain to me <random, obscure="" cve="" vuln="" i="" don’t="" expect="" them="" to="" know="" about=""> and how you would go about exploiting it? </random,>
- 10. What do you do for fun when you aren’t in front of a computer?
- 15 Intermediate cybersecurity interview questions and answers
- 11. What are your top 3 must-have tools for an AD-centric pentest and why?
- 12. How would you perform internal network discovery during a black box internal pentest?
- 13. What is LSASS?
- 14. How could you gain a foothold in AD by targeting a printer?
- 15. How could you confirm a blind command injection or blind stored XSS?
- 16. How would you handle a client dispute of one of your findings?
- 17. Describe various ways that a remote internal penetration test can be performed (from an infrastructure/setup standpoint)
- 18. Describe your note taking/documentation process during a penetration test
- 19. What is union-based SQL Injection?
- 20. What is XXE and what can it be used for?
- 21. What is an IDOR vulnerability?
- 22. Describe your phishing methodology
- 23. How do you prioritize what findings to report?
- 24. How do you assign risk to a finding?
- 25. What would you do if you discovered illegal activity in a client’s network during an internal penetration test?
- MrB3n’s advice for hiring managers and job seekers
- 5 Advanced cybersecurity interview questions and answers
- 26. Describe an XSS vulnerability in high-level terms. Ideally, as if you were explaining it to someone with only high-level technical knowledge.
- 27. You are on your last day of an internal penetration test. You just discovered that you can exploit a development testing server and gain Domain Admin privileges. The exploit has a probability of 8% to crash the server. What do you do?
- 28. You are performing a red team assessment. From the information-gathering phase, you discovered an external company that seems to be white-listed in their defense system. How can you exploit this?
- 29. You are performing an internal penetration test. You discovered that a MAC filtering system prevents you from gaining access to system A. System B can successfully access system A. Any idea of how to compromise system A?
- 30. Your goal is to get access to an administrator’s private VPN keys. You finally got access to the administrator workstation. From Firefox dump, you get a lot of credentials, and you also read some messenger messages indicating that he has sent the VPN keys to his Gmail account. What would you do?
- Acing cybersecurity job interviews
- Keep your skills sharp!
The cybersecurity industry is similar to a professional sports league: heavily skills-based and highly competitive.
As security professionals, this requires us to be smarter, faster, and more skilled than criminals at their own game. If you’re seeking work in the industry, this means acquiring up-to-date skills and then proving to organizations that you have what it takes to help protect them.
If you’re hiring talent, this means knowing how to attract, discover, assess, and grow valuable employees. Interviewing potential candidates is a key part of this cybersecurity recruitment process.
In this guide, we provide the following to assist both interviewees and recruiters:
-
Insights on the cybersecurity job interview processes informed by the personal experiences of industry professionals (who have decades of experience).
-
A list of 30 modern cybersecurity interview questions and answers to assist hiring managers and job seekers.
-
Example answers that can help candidates understand what employers are looking for.
-
Ideas on communicating your cybersecurity skills (even if you have never officially worked in the industry).
|
Skip to the sections of this guide you're most interested in👇 |
10 junior cybersecurity interview questions and answers

👉The first 10 questions were provided by Ken Nevers, CSO/Lead Tester at Red Seer Security and Managing Partner of Hack Red Con. The answers were provided by the author of this post Robert “ltnbob” Theisen.
1. What is penetration testing, and can you explain the difference between vulnerability scanning and pentesting?
💡Interviewers ask this question to see if the candidate understands what a pentester does and can see the bigger picture of why organizations undergo them.
Answer:
“A penetration test is an organized, targeted, and authorized attack that tests the security posture and defensive capabilities of IT infrastructure.
Normally, there’s a specific agreed-upon time frame that a penetration test will span, rules of engagement, and a clearly defined scope.
In the end, the expected deliverable is a detailed penetration test report that security teams can use to mitigate any vulnerabilities that were discovered.
Penetration tests are important because they are a great way to check if your security controls and processes are actually working. Without conducting penetration tests, I believe organizations can have a false sense of security.
A simple comparison I keep in mind is that pentesting is like checking if the door to your home is actually locked and the alarm is armed.
I may think “Did I actually lock my door and arm the alarm?” I can turn around and check by trying to open the door.
A penetration test takes this a step further and emulates a malicious attacker without all the destructive elements.
It makes sure the security controls are doing what they are expected to do. Or even identifies the need for security controls where there are none.
The main focus of a vulnerability assessment is to identify and categorize risk associated with vulnerabilities discovered in IT assets. Typically they are conducted using automated scanning tools like Nessus or OpenVAS.
They are commonly conducted as completely different assessments than penetration tests and do not focus on penetrating further into the network environment through the active use of exploits and attack chaining.
Organizations often have a vulnerability assessment done because they are required to for compliance reasons.
PCI-DSS (Payment Card Industry Data Security Standard) is one example, they require an internal and external vulnerability scan quarterly as outlined on page 23 of the PCI DSS v3.2.1 Quick Reference Guide.
That said, a vulnerability assessment is not as comprehensive as a penetration test.”
Hack The Box content to help you answer this question in an interview:
Interested in landing a job as a SOC analyst? Brush up on these SOC analyst interview questions!
2. Can you describe the different phases of a typical penetration testing engagement?
💡Interviewers typically ask this interview question to see if the candidate understands how a penetration tester typically approaches an engagement.
Answer:
“The phases and the order in which they are done can differ depending on who you talk to. In general, these are the phases of a penetration test, many of which will be repeated as the test progresses:
-
Pre-engagement
-
Information gathering
-
Vulnerability assessment (as a phase built-in to the pentest)
-
Exploitation
-
Post-exploitation
-
Lateral movement
-
Post-engagement
During the pre-engagement phase, all of the important work (not as exciting) is done to ensure all relevant parties understand and document the details and expectations of the test.
At the information-gathering phase, the test and fun begins. This is where I start doing open source intelligence (OSINT) and enumerating hosts, the network, and any reachable services.
I will be documenting any promising findings that the client should know about, like:
-
Unexpected services and IP subnets that are reachable.
-
Secrets found in public-facing GitHub repos, AWS S3 buckets, and other cloud storage technologies.
-
Social media activity from employees that may reveal what technologies are used at the company (commonly found on job descriptions).
-
A visual network diagram to assist me in enumeration and discovery throughout the engagement.
At the vulnerability assessment stage, I start using the information we gathered to determine if there are any vulnerabilities present that can be exploited.
I might start looking up known vulnerabilities based on service and software versions, noting any CVEs, finding proof of concept exploits (PoCs), and carefully planning the attack attempts.
At the exploitation phase, I’ll perform the attack and/or series of planned attacks to attempt to exploit any vulnerabilities.
If I have been brought on to test an environment externally and internally, I will be attempting to exploit a vulnerable public-facing system to see if the vulnerability will allow me to pivot from that external-facing system onto internal IT infrastructure.
There are some companies that still host their own websites on-prem in a DMZ, but it is more common for companies to use 3rd party website hosting services or cloud providers for website or web application hosting.
If the engagement calls for me to test from the internal perspective, my contact will provide me with remote access via virtual private network (VPN) or even use an attack VM that gets spun up somewhere on their internal network environment.
Regardless, I will document each attack I attempt (successful and unsuccessful), including the date and time for full transparency.
In the post-exploitation phase, I will check to see what kind of privileges the account I landed on has. If it is a Windows system I’ll run a series of commands to live off the land, discover interesting files, and find potential pathways for privilege escalation, including but not limited to:
-
whoami /priv
-
ipconfig /all
-
netstat -antp
-
arp -a
-
Systeminfo
-
wmic qfe get Caption, Description, HotFixID, InstalledOn
I’ll also look for any interesting files on the system using a series of search-centric commands and scripts (example: WinPEAS) that are configured to look in common directories using keywords that may find files containing sensitive information.
Depending on how secure the environment is, I may choose not to run any type of pre-made scripts to attempt to avoid any potential detections. That said, I understand that it isn’t always bad to get detected as a tester.
It helps the organization see what they are doing right as well, I just wouldn’t want the engagement to end too soon 😊.
At the lateral movement phase, I will use information gathered from what I did in post-exploitation to determine if I can—and how I should—try to move laterally to another system on the network.
Lateral movement and post-exploitation are very closely related, as are all the phases. This may mean that I discover the Windows system I land on is part of a Windows domain, and I try to harvest domain user credentials that I could use to remotely access another system on the network through WinRM.
During the post-engagement phase, the report will be prepped to be delivered to the client. I would, of course, use whatever template our company uses to remain in line with our quality standards, operational practices, and style.
As a team, we may come together to discuss the scoring of each vulnerability to communicate impact and prioritize mitigation based on severity.
We would also work with the client to schedule a time when we can discuss our findings with all the relevant stakeholders.”
Hack The Box content to help you answer this question in an interview:
-
All Hack The Box Academy modules in the Penetration Tester Job Role Path
3. How would you handle sensitive data or information you come across during a penetration test?
💡Interviewers may ask this cybersecurity interview question to see if candidates understand the ethical implications and responsibilities that come with being a penetration tester.
Answer:
“Every vulnerability discovered on a client’s network can technically be considered sensitive data or information. Our job as a pentesting team is to help our clients improve security and teach them how they can do so.
As we document our findings, we must be careful and responsible with client data as we’re trusted to do right by them. Suppose we are doing a test for a healthcare provider. It is not my job as a tester to go poking around a database of protected health information (PHI) out of curiosity.
It is my job to discover the vulnerability in the system and understand the impact and potential risk it poses for the client.
Then, document this in a report and deliver it to the client. Some information will be redacted, but we, as a pentesting firm, will likely be keeping a copy of that report on our own company-owned systems.
(We will want to ensure reports are stored on encrypted drives and when moved around over the network, that protocols and message systems use the strongest encryption possible.)
It is also possible that a tester can come across certain information on a system that may be considered illegal content. If this happened to me I would immediately stop the test and consult with my supervisor.
We would likely then communicate the details of what was found and we may even consult with our own legal counsel on how and if we should proceed.”
4. How do you stay up-to-date with the latest security vulnerabilities and attack techniques?
💡Interviewers may ask candidates this question to see their continuous learning strategy.
Answer:
“I use a mixture of passive and active learning to stay updated. Of course, I’m on social media sites like LinkedIn, Twitter and YouTube. I’m intentional about following people who post IT and cybersecurity-focused content.
I also subscribe to newsletters like SANs NewsBites. I’ve found this method is faster than waiting on traditional news and media outlets. It is also fun as I may be sitting on the couch or relaxing while learning.
My favorite resources to follow are:
I also like active learning using sites like Hack The Box because this helps me realize the impact and reality of what is mentioned in the news.
The Academy modules and Boxes that get released are often inspired by recent vulnerabilities that have been discovered in the industry.
Often I may come across a post on Twitter that links to a GitHub repo with a PoC exploit for a vulnerability found in Active Directory or something, and I'll try that PoC in my own home lab. I did this with NoPac when it was first announced.
As soon as I saw it work on my lab domain controller, I immediately started notifying my friends and contacts who lead security teams so they could mitigate.”
5. Do you have a home lab? If so, tell me about it.
💡Interviewers may ask candidates this question to see if candidates practice at home. Many IT and cybersecurity professionals have home labs and build relevant experience through personal projects.
Answer:
“I absolutely do have a home lab. Would you like to see a picture?
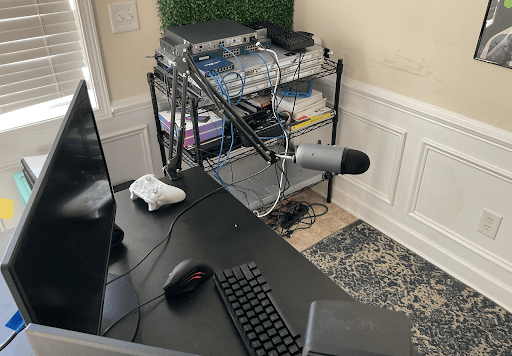
Forgive the messiness. On top of my rack are some switches, routers, and four older Dell PowerEdge servers I got from a friend. This was set up for a video I created to teach people how routing and VLANs work in real life.
Part of my approach to building my home lab is to mimic the real world as much as possible. This not only keeps my skill set sharp but also helps others do the same through various forms of content creation.
I use the server hardware to experiment with virtualizing IT infrastructure through the use of tools like VMware ESXI, XCP-NG, KVM, and others.
Oftentimes I read about a new vulnerability, exploit, and/or attack technique, then try it out on one of the Windows or Linux VMs running on the servers. My home lab is always evolving based on what I want and need to learn next.
Aside from learning outside of work hours, having a home lab is also a great tool during an assessment. If I come across a vulnerability that is tricky to exploit or could potentially cause system instability, I could build a replica of the host in the target environment and attempt exploitation in a safe and controlled manner.
This would give me more information to contact the client about whether or not they would like me to try the exploit in their environment or just document it and move on.”
6. What is your rank on HTB or other platforms, and do you prefer to participate in CTFs with a team or by yourself?
💡Interviewers may ask candidates this question to assess a candidate's independent learning activities and gain insight into how they might or might not fit in with a testing team.
“My rank on HTB is currently Hacker.
I spend a lot of time working on retired machines because HTB allows players to make content based on retired machines.
One of my favorite ways to learn new things is through live streaming, writing, and/or making instructional video content.
When I am feeling competitive and want to rank up, I'll work on active HTB content to earn points.
I personally prefer to approach CTF competitions as part of a team. I love bouncing ideas off of other creative thinkers to solve technical challenges. My first love was basketball, and it instilled in me a competitive drive that I still apply to this day in IT and cybersecurity.
That said, I can approach CTFs or tasks as an individual as well. But I firmly believe in most cases a good team can accomplish far more than any lone individual.”
7. Do you volunteer at security conferences or local infosec meetups?
💡Interviewers may ask a candidate this cybersecurity interview question to demonstrate the organization’s prioritization of outreach and giving back to the community as a whole.
Answer:
“Yes, I do have experience volunteering at conferences. More recently, I gave a talk and training at a conference held at Kennedy Space Center called HackSpaceCon.
I gave a talk on the state of IT and cybersecurity education and conducted training on the fundamentals of computer networking.
Conferences are my favorite way to learn because you network with other people from different walks of life and perspectives that can introduce you to TTPs, concepts, and trends that may not be formally documented anywhere yet.
Plus, you can give back to the community in a major way.”
8. What is your favorite Linux distribution and why?
💡Interviewers may ask candidates this question to see if they have hands-on keyboard experience using Linux. (Unfortunately, a lot of collegiate-level programs are graduating “cybersecurity majors” without any Linux knowledge whatsoever. Also, their answer can provide insight into their personality.)
“This may be an unexpected answer but Linux Mint is my favorite Linux distribution and I'll tell you why. It helped me overcome my intimidation of learning Linux. I laugh at myself thinking that at one time I was intimidated by learning an OS.
A good friend of mine named Rob (known online as rwxrob) helped me get started with learning Linux through using Linux Mint. He encouraged me to try Linux Mint because it looks similar to Windows with the start menu and other Windows-esque visual elements.
I figured out a way to run it on a Surface laptop and just used Linux Mint as my daily driver OS for 6 months. Most of my IT background is in Windows administration and for much of my career, I didn’t really need to know Linux for the networks I was administering and securing. I don’t use Linux Mint much anymore.
I’ve moved on to mainly using Parrot OS, Kali, or Ubuntu but am pretty comfortable on any distro given the task at hand. I also do not get too tribal about Linux distros and remain open-minded to learning new things all the time. Even if it is from Arch Linux loyalists :). As long as VIM is installed over Nano :).”
9. Explain to me <random, obscure CVE/vuln I don’t expect them to know about> and how you would go about exploiting it?
💡Interviewers may ask candidates this cybersecurity interview question to gauge a couple of things:
-
Their willingness to admit that they don’t know the answer.
-
How they would go about researching and learning something they don’t understand.
-
How they think on their feet and react to unexpected events.
Answer:
“I am not familiar with that <CVE/VULN>. I’ll have to do some research and get back to you on that. If you have some good leads, links, or ideas on it, would you mind sharing?”
Hack The Box content to help you answer this question in an interview:
10. What do you do for fun when you aren’t in front of a computer?
💡Interviewers may ask candidates this question to get a glimpse of your character, what you are passionate about besides hacking, or what team or manager you fit in with.
Answer:
“I find great joy in learning and doing various things on the computer, including but not limited to home labbing, Hack The Box, and video games. When I am not at the computer I enjoy traveling to scenic places with my family.
Recently I’ve been drawn to the mountains because I find the views inspiring. Spending time with family is essential on these scenic trips. I also like taking my son to the park to play basketball.
He is getting to the point where he can dribble the ball, and I’m excited to see him start to shoot threes on his own. I listen to a lot of podcasts and music as well.”
Ken’s career advice for job seekers
-
Force yourself to be extroverted if you aren’t naturally. Speak in front of others, and interact with people outside of the internet. At the end of the day, pentesting is a customer service role. It requires you to befriend and communicate effectively both in spoken and written forms with your customers, coworkers, etc.
-
Volunteer at conferences. Seriously, this will get you rubbing shoulders with industry leaders, give you job referrals, and improve your communication skills. It’s a whole lot easier to get that interview when referred to HR by the CEO of the company that you formed a relationship with at a con, than via a recruiter from LinkedIn.
-
Go after hands-on certifications. Passing a practical certification exam (emphasis on “practical”) demonstrates your ability to actually do different aspects of the job: learn new skills, perform under pressure, and write real-world reports.

15 Intermediate cybersecurity interview questions and answers
👉The 15 intermediate cybersecurity interview questions were provided by Ben Rollin, Hack The Box’s Head of Security and one of the lead visionaries behind HTB Academy. The answers were provided by the author of this post Robert “ltnbob” Theisen.
11. What are your top 3 must-have tools for an AD-centric pentest and why?
💡Interviewers may ask candidates this question to see how well candidates understand Active Directory pentesting.
Answer:
“My top 3 AD-centric tools are:
BloodHound because it is a comprehensive AD enumeration tool that creates a nice visual map to quickly visualize relations between AD objects, domain, trusts, group policies, group permissions, and more. It quite literally helps me see different attack vectors.
PowerShell because it is already built-in to Windows clients and servers. I like to live off the land whenever possible. Most IT admin teams are already using PowerShell for administrative tasks and many of those same tasks can be useful for pentesters during a pentest.
One example of this would be the ActiveDirectory PowerShell module. This allows admins to interact with AD through the PowerShell command line on a Windows host.
If I was able to find my way to an IT admin’s desktop I may just be able to use their system to gain remote access to the domain controller. Especially if they are using the AD PowerShell module in their daily work.
PowerView.ps1 which is part of the PowerSploit project because it has so many useful tools for enumerating AD objects, discovering shares, and even harvesting TGS tickets to attempt a Kerberoasting attack.”
Hack The Box content I recommend you use to help you answer this question in an interview:
12. How would you perform internal network discovery during a black box internal pentest?
💡Interviewers may ask candidates this question to see how they would approach discovering a network having been provided very little information about the network.
“How I would proceed would depend on whether I was starting from one of the organization's devices or my own attack system.
If I did not have a network connection already, I would see if I could find an open network drop somewhere in the building or a wireless network to connect to.
In general, I would begin by trying to discover all the hosts on the network using a tool like an advanced IP scanner, angry IP scanner, Nmap and even just running a ping sweep script (PowerShell or Bash-based).
If the wireless networks are in scope I may even use a mobile phone or tablet with an app like Fing to attempt to discover hosts on the network.
I’d immediately begin documenting discovered hosts in order to start building a topology for myself to start understanding what the network security looked like and where critical systems may be.
I would also keep it simple and use built-in OS commands like ipconfig/all traceroute, and ip add to identify default gateways (routers), DHCP servers, and DNS servers (DNS servers are normally Domain Controllers in Windows-based environments).”
If I am starting from a Linux testing box or my laptop inside their network, I would run Wireshark or tcpdump for 20 minutes or so and then analyze the data. This would most likely give me some information I can use to start mapping the internal network.
If the testing box I am on has working DNS I could do an “nslookup acme.local” (nslookup against the client’s AD domain) and see what Domain Controllers/DNS servers come back.
If I see, say, eight results all in different subnets I could proceed with additional discovery against the /24 networks that those domain controllers sit in and even include a network 1 third octet up and 1 down for each discovered subnet. (i.e., if a domain controller is at 172.16.2.3 I could include 172.16.2.0/24. 172.16.3.0/24, and 172.16.4.0/24 in my target list for further enumeration.)
Another way to discover hosts would be doing a List Scan using the Nmap -sL flag against subnets around the one my host sits in or even against all private IP ranges.
This will perform reverse DNS lookups without sending any packets to the individual hosts. It can be a stealthier way to map the network, but will likely come back with plenty of hosts that exist in DNS but are no longer “live” on the network.
Hack The Box content to help you answer this question in an interview:
13. What is LSASS?
💡Interviewers may ask candidates this cybersecurity interview question to gauge their understanding of one of the ways Windows handles credentials.
Answer:
“LSASS is the Local Security Authority Subsystem Service in Windows operating systems that enforces security policy.
On an engagement, if I have successfully compromised a Windows system, one of the first things I will try to do is dump LSASS memory.
Inside LSASS memory, there is information that may help with lateral movement and privilege escalation. This includes:
-
Password
-
Password hashes (NT & LM)
-
Kerberos Tickets
After obtaining one of these I could attempt to Pass The Hash (PtH) and/or try to crack one of the hashes. If it is an older or misconfigured system, I may also get lucky and get the clear text password for an admin-level user.”
Hack The Box content to help you answer this question in an interview:
14. How could you gain a foothold in AD by targeting a printer?
💡Interviewers may ask candidates this question to see if they are familiar with unique ways to test the security of Active Directory.
Answer:
“Organizations that have one or multiple physical locations will most certainly use printers in their environments. Some employees will have different printing needs, and usually, this functionality is controlled and accounted for by enforcing authentication through Active Directory.
Essentially, before users can actually complete a print job they will need to have a Domain User account that is authorized to print. This said, the web-based configuration interface of the printer itself is often forgotten and left at default settings.
This may allow for login using default credentials. I would navigate to the IP address of the printer using a browser and attempt default credentials. If I could log in to the printer I would look for configurations that tell the printer to point to Active Directory for authentication.
There have been known vulnerabilities in certain printer models that allowed one to configure the LDAP settings to point to an attack system instead of an LDAP server or AD.
If this were the case, I would change the IP in the LDAP settings to my own attack system and start a listener to see if I could capture any domain credentials that I could use to gain a foothold in AD.”
Hack The Box content to help you answer this question in an interview:
15. How could you confirm a blind command injection or blind stored XSS?
💡Interviewers may ask candidates this question to gauge their understanding of common web-based attacks.
Answer:
“Assuming I have already discovered the vulnerable parameter or form that is vulnerable in the web application, I will try to confirm a blind command injection through the use of commands that would generate network traffic or a call back to my attack system.
I would do this because with blind command injection the output of the injected command would not likely be returned to the browser anywhere on the web page, hence why it would be blind.
The simplest first command to send is a ping against my own attack system: ping <ipAddressofAttackSystem>
On my attack system I will have started a packet analyzer like Wireshark or tcpdump and I'll look for any ICMP requests coming from the target.
If I see ICMP requests coming from the target then the blind command injection vulnerability has been confirmed, and I would know that the web server was executing my injected command.
A failed ping will not always mean that command injection is not possible due to potential network configurations that may disallow pinging our attack host from a target machine. Nonetheless, it's a great first step.”
Hack The Box content to help you answer this question in an interview:
16. How would you handle a client dispute of one of your findings?
💡Interviewers may ask candidates this question in order to understand how the candidate handles client relations.
Answer:
“This would depend on the exact finding a client is disputing. Penetration testers can make mistakes, like anyone else, and we may have reported a false positive or need more context from the client regarding their environment to incorporate mitigating controls into the finding writeup.
In general, I would like to meet with them via a virtual or in-person session (if that is what they prefer) so I may clearly understand their concerns and disputes. It could be the case that they need assistance to better understand the finding or perhaps I made a mistake that needs correcting.
If they were claiming that one of my findings isn’t true I would provide further evidence such as screenshots, logs, or even demonstrate to them live.
Either way, I would take their concerns and dispute seriously then proceed accordingly to ensure they are happy with the service provided. I would keep my manager in the loop throughout the process.
If I was not able to handle the dispute directly I would work with my manager to escalate it to the leadership level.”
Hack The Box content to help you answer this question in an interview:
17. Describe various ways that a remote internal penetration test can be performed (from an infrastructure/setup standpoint)
💡Interviewers may ask candidates this question to see if they understand how remote pentesting is conducted in practice:
“There are a variety of ways we could do remote internal pentesting. We could set up our own virtual machine with all of the tools we will need for the assessment, then provide the client’s IT/security team with the instructions on how to download it and set it up on a hypervisor connected to their internal network.
Our VM would have our remote access software pre-installed so that the tester, or team of testers, can have access from their home or our offices.
We could also ship the client an appliance (pentester in a box) that we have preconfigured with all our tools. We would provide them with instructions on how to set up and connect the appliance for the tester or team of testers to remotely conduct the test.
Most remote access tools use hyper text transfer protocol secure (HTTPS) to connect to the client, so we may be good to go as soon as the client connects the appliance to the network.
With either the VM or appliance approach, it may be best to also request the client provide us with temporary VPN access for the duration of the test to add an additional layer of encryption on top of the encryption used by our remote access tools.”
Hack The Box content to help you answer this question in an interview:
18. Describe your note taking/documentation process during a penetration test
💡Interviewers may ask candidates this question to get a good understanding of how they will take notes and put together a report.
Answer:
“I will take notes and screenshots throughout the duration of a test. For each enumeration and attack attempt, I will document and log for CYA (Cover Your Anatomy) purposes.
If the pentesting company is standardizing on a single note-taking tool, then I will be sure to use that. However, I default to CherryTree, Typora, or other offline note-taking tools.
Any major findings or key information that should be in the report I will put into the pentesting report template the company uses. I’ll paste it in and perfect it at the end of the test, but will be sure to capture the most important output, screenshots, and findings as soon as I find them.
There are many details that can be encountered during a test that can get lost if they aren’t documented immediately. Human memory can be unreliable, that is why we have computers.
I also keep a separate knowledge base of notes where I keep links to different new resources I may come across. It is a playbook that may assist me in applying those TTPs in other engagements I may be on or practice on Hack The Box content.
I add to this playbook as I study and learn on Hack The Box as well. I do not include any client information in this playbook, only TTPs and links to public resources (blog posts, YouTube videos, etc.).”
Hack The Box content to help you answer this question in an interview:
19. What is union-based SQL Injection?
💡Interviewers may ask candidates this question to gauge a candidate’s understanding of different types of SQL injection attacks.
Answer:
“The term ‘union’ in Union-based SQL injection refers to the SQL UNION operator, which combines the results of two or more SELECT queries into a single result set.
In a Union-based SQL injection attack, an attacker appends a crafted UNION SELECT statement to the original query to force the application to return additional data that was not intended to be disclosed.
During a penetration test, I would attempt to identify Union-based SQL Injection vulnerabilities by carefully examining how user inputs are handled in the application. I'd look for potential points of entry where untrusted data is used in SQL queries without proper validation or parameterization.”
Hack The Box content to help you answer this question in an interview:
20. What is XXE and what can it be used for?
💡Interviewers may ask candidates this cybersecurity interview question to gauge a candidate’s understanding of XML external entity injection attacks.
Answer:
“XXE occurs when an attacker can inject malicious XML data into an application's input fields, which is then processed by the server. When the server parses the XML, it may include external entities defined within the XML data, leading to unintended consequences.
My focus would be to identify and exploit XXE vulnerabilities in web applications to demonstrate their impact and potential risks to the organization.
I would use a combination of manual and automated testing techniques to detect and verify these issues. This includes fuzzing, payload injection, and examining application behavior in response to different XML inputs. A wide range of critical actions and information can be gathered through this kind of attack, including but not limited to:
-
Information Disclosure: Attackers can read files from the server's filesystem by specifying external entities that point to local files. This can reveal sensitive information like passwords, configuration files, or system data.
-
Denial of Service (DoS): Attackers can trigger resource-intensive processing by defining large external entities, causing the server to consume excessive CPU and memory resources and potentially leading to a denial of service.
-
Server-side request forgery (SSRF): Attackers can abuse XXE to make the server perform unintended HTTP requests to internal or external resources, leading to further attacks like scanning internal systems or accessing sensitive APIs.
-
Port scanning: An attacker can use XXE to scan ports of internal systems, potentially identifying other vulnerable services.”
Hack The Box content to help you answer this question in a cybersecurity interview:
21. What is an IDOR vulnerability?
💡Interviewers may ask interviewees this question to gauge their understanding of common web-based vulnerabilities.
Answer:
“An indirect object reference vulnerability (IDOR) is a vulnerability commonly found in web applications that would allow an attacker to reference a file or object in a database that is intended to be accessed by authorized individuals.
One example of this would be if a web application was hosting a publicly accessible PDF. When the users click the link to the PDF, the object reference in the HTTP request may look like:
?filename=file_1.pdf
An attacker may notice this and attempt to increment file_1.pdf to file_2.pdf and access information that may not be intended to be public.
This could lead to sensitive data exposure and/or indicate weak access control on the backend of the web application.”
Hack The Box content to help you answer this question in an interview:
22. Describe your phishing methodology
💡Interviewers may ask candidates this question to understand a candidate's approach to social engineering.
Answer:
“Business email compromise (BEC) is one of the most common ways that attackers will target and breach individuals and organizations. It collectively costs businesses billions of dollars in losses a year.
Because of this, I believe phishing methodology should be built around interacting with users through email messaging. This can be targeted through OSINT research on social media and/or more generally, through the use of automated tooling that provides IT teams and security firms with analytics that show what emails and links are getting clicked.
Social engineering and phishing are useless without education attached. I have a strong background in education and I enjoy teaching. In using phishing emails and tracking who clicked what, I will connect users to an education program where I will then meet with the user to conduct security awareness training.
My views may differ on this from many testers and researchers in that I do not think social engineering attacks are useful to people unless we teach them what they did wrong in effective ways.
If we aren’t careful and strategic about connecting our engagements with education, social engineering engagements may inspire more of a culture of fear and discourage people from reading emails and/or picking up the phone altogether.
It is not about outsmarting people to brag about how smart we are. It's about empowering people with tools to have the security mindset required to intuitively avoid being fooled by malicious attackers.”
Hack The Box content to help you answer this question in an interview:
23. How do you prioritize what findings to report?
💡Interviewers may ask candidates this question to see if they understand how to communicate impact through the report.
Answer:
“I was able to inject a command through the web application that allowed me to get a reverse shell back to my attack system.
I then escalated privileges on that Linux-based web server because it was vulnerable to CVE-2016-5195 (Dirty Cow), and I got root on the box. It was awesome, you guys need to fix that.”
💡Note: Most business decision-makers will likely not understand such a technical answer, and as a result, the information is not very useful in helping them make good decisions.
Improved answer:
“It is my belief that we have to be good enough communicators to speak technical, risk, and business language in verbal and written form.
In the report, we should prioritize findings based on the most critical security issues. This doesn’t always mean prioritizing based on the coolest attacks and techniques we were able to pull off.
We have to understand the business impact. Suppose we were able to get domain administrator credentials via phishing and business email compromise.
We were also able to get a foothold and root on that Linux-based web server, but the web server was in the DMZ and just hosted how-to docs showing the company's users how to use their products.
I would personally prioritize the finding that allowed us to get domain admin credentials over the web server, even though it is less technical.
The potential impact on the business is greater if an attacker got those domain credentials compared to if they got root on that web server. The client should fix both but we would consider the domain credentials one a higher finding in our report. “
Hack The Box content to help you answer this question in an interview:
24. How do you assign risk to a finding?
💡Interviewers may ask candidates this question to gauge the candidate's understanding of risk within the context of penetration testing.
Answer:
“When evaluating a finding, I would typically follow this line of thinking to assign risk:
-
Impact assessment: I would analyze the potential impact the finding could have on the organization's assets, data, and operations. This involves considering factors such as data sensitivity, business criticality, and the potential for financial loss or reputational damage.
-
Likelihood evaluation: Next, I would assess the likelihood of the finding being exploited by a real-world attacker. This includes understanding the complexity of the attack, the skill level required to exploit the vulnerability, and whether there are any existing mitigations in place.
-
Contextual analysis: It's essential to consider the specific context of the organization and its security controls. For example, a vulnerability might be more critical for an organization that deals with highly sensitive customer data compared to a company that doesn't handle sensitive information.
-
CVSS scoring: I would use the Common Vulnerability Scoring System (CVSS) to provide an objective and standardized score to the finding. CVSS takes into account various factors like exploitability, impact, and ease of mitigation.
-
Communication with stakeholders: Once the risk is assessed, it's crucial to communicate the findings and their potential impact to the relevant stakeholders, such as IT teams, management, or system administrators.
-
Remediation recommendations: I would provide actionable recommendations for mitigating the identified risks. These might include patching systems, updating configurations, implementing security controls, or conducting user awareness training.
-
Risk classification: Based on the overall assessment, I would classify the finding into risk categories (e.g., high, medium, low) to help prioritize remediation efforts.
-
Continual monitoring: Finally, I would emphasize the importance of ongoing monitoring and reevaluation to ensure that the risk landscape remains up-to-date and that new vulnerabilities are promptly addressed.
Hack The Box content to help you answer this question in an interview:
25. What would you do if you discovered illegal activity in a client’s network during an internal penetration test?
💡Interviewers may ask candidates this cybersecurity interview question to see how they perform in high-risk situations.
Answer:
“I would immediately stop the engagement and document exactly what was discovered, including screenshots (being careful not to screenshot anything illegal or illicit), command output, system information, date, and time.
Then I would notify my direct manager of the exact details of what was discovered. I would not proceed with the engagement until I receive instructions from leadership. It is likely that leadership would need to consult with legal counsel on how best to proceed with further interactions.”
MrB3n’s advice for hiring managers and job seekers

If you do not yet have real-world experience, be ready to talk about your blog, GitHub, Hack The Box experience, or any relevant courses/certifications.
Focus on what practical knowledge you gained, any tools you have created or contributed PRs to, and any CTF/vulnerable box write-ups you have done.
If you have CVEs, you could talk about the entire process you followed—from discovery to reporting, acceptance, and assignment of the CVE.
If you have a home lab, be ready to talk about how it's set up, the challenges you faced, and how you use it to learn/practice and stay sharp. You could even screen share and show your own note-taking setup for a retired HTB box or similar.
Another optional but good way to showcase your skills would be to create a sample penetration testing report of a purposefully vulnerable environment.
This could be an Academy module that has a small AD lab or a lab you built.
It doesn't have to be anything massive, but being able to show 1-2 of each type of vulnerability (web, network, AD) and across all risk ratings (high, medium, low, best practice recommendation) will give the hiring manager a great look at your technical skills and how you present your work.
Make sure to spend time getting the Executive Summary solid and ensure that the grammar, spelling, punctuation, and formatting are neat and professional.
This should be a document that would be ready for a quick QA before being delivered to the customer.
To assist you with this process, review the Documentation and Reporting module on HTB Academy, and feel free to utilize the sample penetration test report template we provide!
For hiring managers: The ideas above may help you formulate your questions and get more insight into how a candidate works. While not having any of these shouldn't necessarily disqualify a highly proficient candidate, it can give a window into their skill set and work ethic and help set them apart.
For interviewees: We don't need to live and breathe cybersecurity/pentesting, but since the field constantly changes and evolves, it is imperative to stay on top of the latest and greatest tools and techniques.
If your knowledge and experience are five years removed from the current state of Active Directory pentesting, for example, then you will likely miss high-risk issues in a client environment and be able to add less value than a candidate who is familiar with and has hands-on experience practicing these tools and tactics.
Recommended read: Active directory pentesting cheatsheet
5 Advanced cybersecurity interview questions and answers
👉The five advanced cybersecurity interview questions below were provided by Hack The Box’s Senior Director of Labs, Manos Gavriil (aka Arkanoid). The answers were provided by the author of this post Robert “ltnbob” Theisen.
26. Describe an XSS vulnerability in high-level terms. Ideally, as if you were explaining it to someone with only high-level technical knowledge.
💡Interviewers may ask candidates this question to grasp a candidate's ability to communicate complex technical information in an easy-to-understand manner.
Answer:
“A cross-site scripting (XSS) vulnerability is a type of security issue that occurs when malicious code is injected (e.g., malicious SQL statements) into a website or web application, allowing attackers to execute their code on the browsers of unsuspecting users.
Imagine your website as a house with different rooms for various functionalities. Such as login, messaging, or user profiles.
XSS is like an intruder who finds a way to slip a harmful message or piece of code inside one of these rooms. When an unsuspecting visitor enters that room (opens a specific page or clicks a link), the intruder's code executes in the visitor's browser.
This can have several negative consequences, including but not limited to:
-
Data theft: The attacker can steal sensitive user information, such as login credentials, personal details, or payment card data.
-
Session hijacking: By exploiting XSS, the attacker could hijack an authenticated user's session, gain unauthorized user access to their account and perform actions on their behalf.
-
Malicious actions: Attackers might use the vulnerability to trick users into unknowingly performing harmful actions, such as changing account settings or making unauthorized transactions.
-
Phishing attacks: XSS can be used to present fake login forms, leading users to believe they are entering their credentials on a legitimate website, but in reality, they are providing the information to the attacker.
To protect against XSS, it's essential to follow secure coding practices, validate and sanitize user input, and implement security mechanisms that restrict the execution of untrusted code on the website.”
Hack The Box content to help you answer this question in an interview:
27. You are on your last day of an internal penetration test. You just discovered that you can exploit a development testing server and gain Domain Admin privileges. The exploit has a probability of 8% to crash the server. What do you do?
💡Interviewers may ask candidates this question to see how they will make decisions considering their client's best interest.
Answer:
“I really enjoy seeing exploits work on an engagement and/or in a lab environment like on Hack The Box; however, there are many different factors to seriously consider the impact on the availability of critical business systems.
When testing the security of a system that is in use by a company, it is important to remember why we are doing testing in the first place.
The end goal is to provide the client with security recommendations, raise awareness, and to help them—not to do damage and cause problems because we want to hack.
Knowing that the exploit may bring the server down would deter me from running the exploit at all, especially when it is the last day of the test.
I would document my findings, and share what could have potentially been done and why I did not proceed with attempting the exploit.
I’d share this in the report and in the debriefing meeting with the client.
If the client insisted that we attempt to penetrate because they really want to see the impact and could withstand a temporary outage, then I would get that in writing from an authorized stakeholder and proceed; however, this would be at the client’s discretion.”
Hack The Box content to help you answer this question in an interview:
28. You are performing a red team assessment. From the information-gathering phase, you discovered an external company that seems to be white-listed in their defense system. How can you exploit this?
💡An interviewer may ask a candidate this question to gauge their understanding of how to proceed with testing according to a scope and what the client has authorized.
Answer:
“If I discover an external company that appears to be white-listed to the defense system, it could present an interesting opportunity for lateral movement or bypassing security controls.
However, it's crucial to emphasize that any action taken during a red team assessment must be conducted with the organization's explicit authorization and within the agreed-upon scope of the engagement.
Unauthorized or unapproved actions can have serious legal and ethical implications.
Keeping that in mind, my approach would be as follows:
-
Assessment scope review: I would carefully review the scope of the red team assessment to ensure that any potential actions involving the external company fall within the authorized boundaries of the engagement.
-
Client communication: I would communicate my findings to the client's security team and discuss the potential implications of the white-listed company's access. This would also be an opportunity to understand if this access is intentional or a misconfiguration.
-
Authorization for further testing: If the client agrees and provides authorization, I might proceed with targeted testing against the white-listed company's systems to understand the extent of the access and its potential impact on the organization's security.
-
Lateral movement simulation: I would simulate potential lateral movement scenarios to determine if access to the white-listed company could be exploited to gain unauthorized access to other critical systems or data within the organization.
-
Documentation and reporting: Throughout the process, I would document my actions, findings, and the steps taken during the assessment. This documentation is essential for the client's understanding and for creating a comprehensive final report.
-
Risk analysis and recommendations: In the final report, I would provide a detailed risk analysis, outlining the potential risks and impact of the white-listed company's access. I would also offer actionable recommendations to strengthen the organization's security posture.”
Hack The Box content to help you answer this question in an interview:
29. You are performing an internal penetration test. You discovered that a MAC filtering system prevents you from gaining access to system A. System B can successfully access system A. Any idea of how to compromise system A?
💡Interviewers may ask candidates this question to understand the candidate's approach to defense evasion.
Answer:
“I would attempt to discover the MAC address of system A and try to spoof it on my attack system to see if the MAC filtering system would allow me to communicate to system B from my attack system.
One way I could do this is by pinging system A from my attack system to ensure traffic is generated from my attack system to system A. I know when this happens ARP also has to run to populate the ARP cache (IP address to MAC address mapping). I'd then use the ARP -a command on my attack system to discover the MAC address associated with system A.
Once I have the MAC address of system A, I will attempt to spoof the MAC address using a tool like macchanger to see if I can get past the MAC filtering system.”
A note from Monos💡: Technically, spoofing is the solution. But this question hides a trap and really wants to check the experience and professionalism of the penetration tester. By spoofing the MAC address it’s possible to create Denial Of Service conditions by having MAC conflict. Thus, before actually performing this attack, it would be wise to ask about permissions.
Hack The Box content to help you answer this question in an interview:
30. Your goal is to get access to an administrator’s private VPN keys. You finally got access to the administrator workstation. From Firefox dump, you get a lot of credentials, and you also read some messenger messages indicating that he has sent the VPN keys to his Gmail account. What would you do?
💡Interviewers may ask candidates this question to assess their decision-making process when in a situation where ethics and scope may need to be strongly considered before proceeding.
Answer:
“I would proceed with caution. In most cases, people’s personal social media accounts and email accounts are not in scope for ethical and legal reasons. That said, I would not proceed with attempting to access any of their personal accounts.
I would instead move on to seeing if I could access their work email account to see if I could get access to the virtual private network keys via their Sent mailbox. This could be done via the browser or looking for a locally installed email client application like Outlook, Thunderbird and/or Mail that is likely already signed in.
I would include all this in the report and suggest that this employee refrain from accessing personal accounts from company-owned computers or using their personal accounts to handle sensitive business-critical data.”
Acing cybersecurity job interviews
The ultimate purpose of a cybersecurity job interview is to find the right candidate who can meet an organization's current needs, future goals, and expectations.
Typically, you’ll go through multiple rounds of interviews, sometimes conducted by a team. This approach is common as it helps bring diverse perspectives to the hiring process and ensures the best person is chosen for the job.
The interview panel can consist of non-technical individuals familiar with HR processes and organizational culture, as well as subject matter experts (SMEs) who understand the technical aspects of the role. You should be prepared to communicate with both types of interviewers to make a strong impression.
Remember that your answers don't need to be perfect. It’s not about knowing it all. In fact, I’d suggest refraining from trying to convince interviewers that you know everything, as honesty and self-awareness are valuable traits during the interview process (and in general).
Hiring teams are more interested in finding someone they can enjoy working with, and who has relevant skills, knowledge, and experience to get started quickly in the role.
Finally, practice mock interviews with friends and family to exercise your communication skills and improve your ability to present under pressure.
Keep your skills sharp!
Please know these are just some of the cybersecurity interview questions you may come across during an interview. As you prepare for your next interview, be sure that you are actively working towards keeping your skillset sharp.
You don’t have to know everything, but you should be able to know at least what to do next. For the topics you do know, be sure to provide as much detail as possible to show the interviewer your thinking process, approach, knowledge, and methodology.
The team at Hack The Box will always be here to support you along your journey. Until next time, keep learning!
|
Author bio: Robert Theisen (LTNB0B), IT Program Director/Cybersecurity Professor Robert loves learning, but he loves to empower others even more. He never takes off his IT/infosec professional hat and never will so long as he is preparing others to succeed by mastering the various tactics, techniques, procedures, and tools at their disposal. He has been in the industry for over 10 years, accumulated over 10 certifications, and assisted thousands of people around the world with entering and leading successful careers in the industry. None of his accomplishments would be possible without great mentors, friends, family, the Internet, and God. You can connect with him on LinkedIn. |







