Hacker
How to become a cybersecurity engineer: ultimate career guide
Wondering what it takes to become a cybersecurity engineer? Here’s a complete career guide with insights from experienced security professionals!

KyserClark,
Nov 07
2023
Table of Contents
From monitoring network traffic to hardening system security, cybersecurity engineers are the “fortress builders” of cyberspace.
But what does it take to become one?
This comprehensive career guide is for professionals hungry for that next big step, as well as curious minds venturing into information security. You’ll learn about the essential skills required to become a cybersecurity engineer and how to flourish in the role!
What is a cybersecurity engineer?
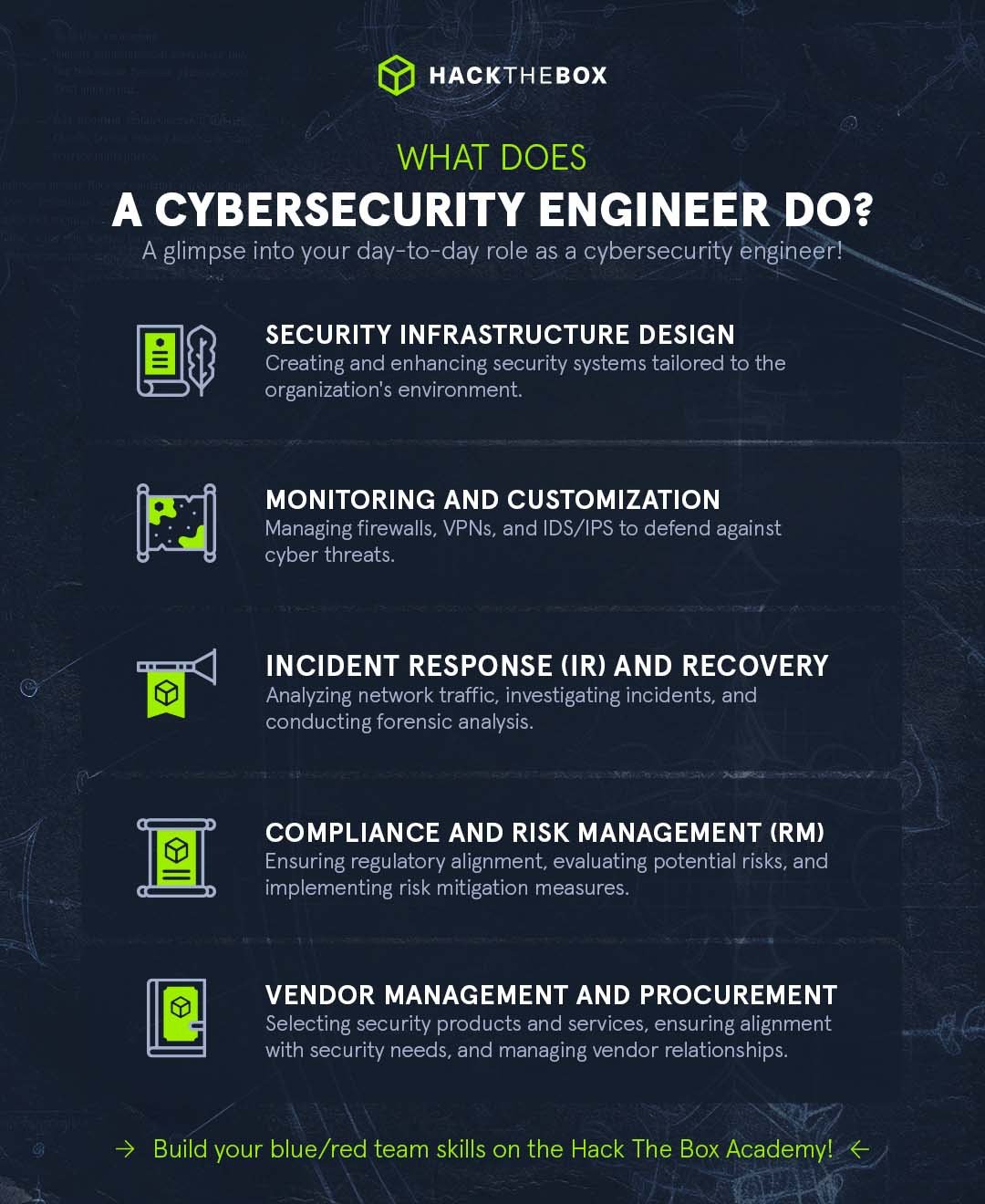
A cybersecurity engineer is a “digital fortress builder” entrusted with the blueprints and keys to safeguard an organization’s critical infrastructure and assets from emerging threats.
Their main duties revolve around designing and improving security infrastructure around an organization's unique environment. This includes the monitoring and customization of firewalls, VPNs, or intrusion detection/prevention systems (IDS/IPS) to build barriers against malicious cyber attacks.
A cybersecurity engineer is also involved in:
-
Incident response (IR) and recovery: Employing their expertise in network traffic analysis, cybersecurity engineers respond to incidents, investigate the root cause by (conducting forensic analysis and isolating affected systems), and remediate to restore normalcy.
-
Compliance and risk management (RM): Ensuring alignment with regulations and standards like the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), or The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF). Cybersecurity engineers evaluate potential risks and implement measures to mitigate them. This involves continuously assessing security policies and controls and adjusting strategies to meet evolving compliance requirements.
-
Vendor management and procurement: Working with external vendors, cybersecurity engineers evaluate and select the right security products and services. This involves negotiating contracts, ensuring the products align with the organization's security needs, and managing ongoing vendor relationships.
-
Disaster recovery (DR) planning: Crafting and maintaining a DR plan ensures the organization is prepared to respond to any catastrophic event. This includes defining and regularly testing procedures (with tools such as tabletop exercises) to restore systems and data after a significant failure or attack.
Cybersecurity analyst vs. cybersecurity engineer
A cybersecurity engineer's responsibilities can overlap with a cybersecurity analyst's. So understanding each role's distinct functions is key to selecting your career path.
Think of the analyst as the “security sentinel” patrolling the castle grounds, watching for any signs of trouble. On the other hand, the engineer is the “builder” or “architect”. He constructs the “castle's” defenses. And fortifies it against potential threats whilst ensuring it remains accessible to everyday residents.
The responsibilities of an analyst or engineer will often vary depending on the organization they work for and their seniority. So it's difficult to nail down exactly what an “analyst” or “engineer” would usually do (as I don’t really think there is or should be a “usual”).
Sebastian Hague, Defensive Content Lead, Hack The Box
Start your cybersecurity career with HTB CDSA

Why choose HTB Certified Defensive Security Analyst (CDSA)?
-
Start as a noob. Finish as a “job-ready” professional. CDSA is beginner-friendly certification that leaves you with intermediate-level skills upon completion. Stand out to recruiters and hit the ground running!
-
Highly hands-on certification that builds and tests your analysis, SOC operations, and incident handling skills in real-world environments. (You’ll have to compose a commercial-grade security incident report to pass.)
-
Stand out with unique skills: HTB is recognized for content that builds creativity, in-depth knowledge, and outside-of-the-box thinking required for real-world incidents.
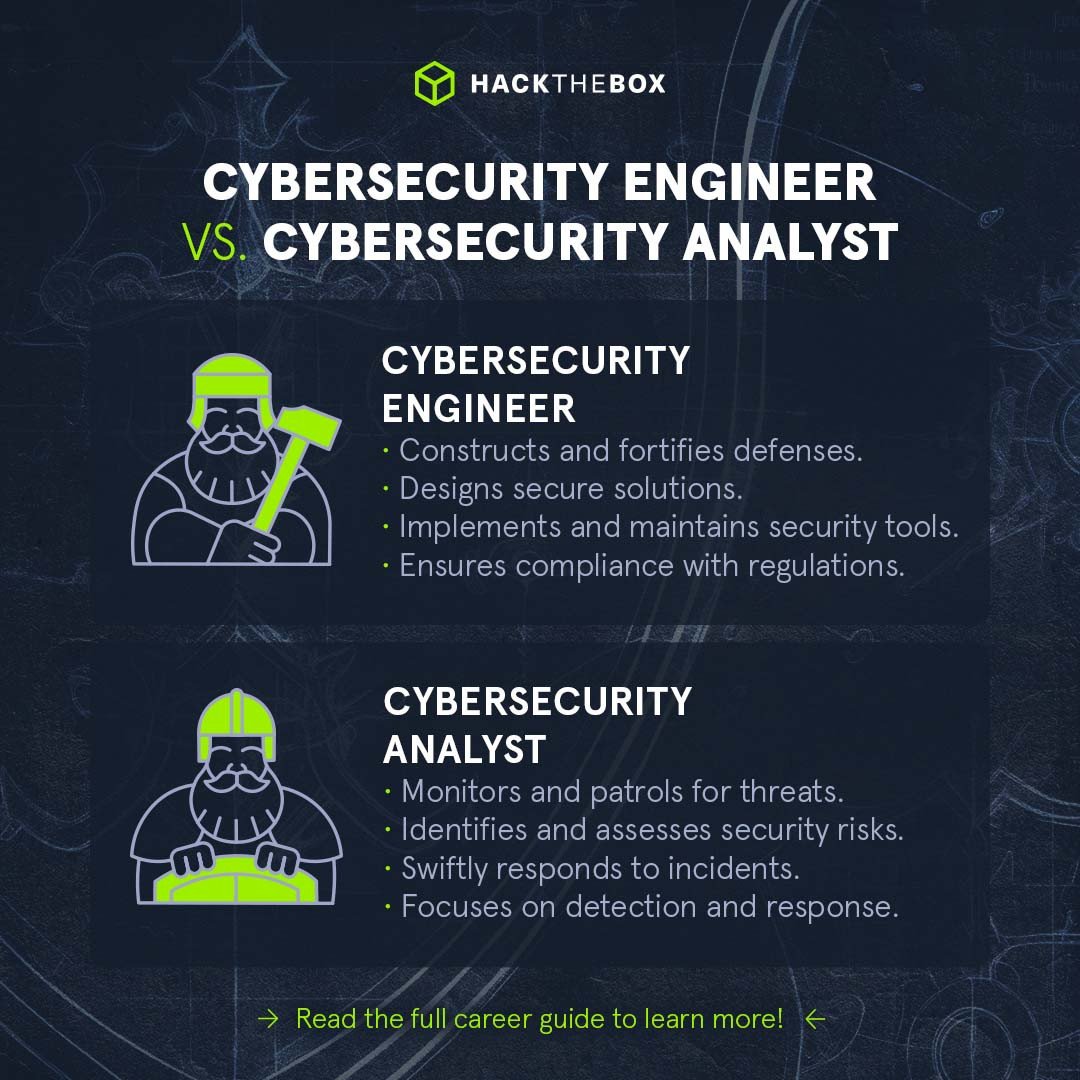
Here’s a breakdown of each role's “traditional” responsibilities:
Cybersecurity analyst
As the sentinel on the “frontline” of digital warfare, analysts play a critical role in safeguarding digital assets and protecting sensitive information from malicious threat actors.
Their role is to identify security threats, assess the impact of those threats, and, in some cases, take necessary actions to prevent or mitigate any damage. Their core responsibilities are:
-
Threat analysis: Identifying and evaluating potential risks and vulnerabilities.
-
Monitoring: Constantly scrutinizing system activities for unusual patterns.
-
Incident Response: Reacting swiftly to breaches, analyzing them, and implementing solutions to prevent future occurrences.
If becoming a cybersecurity analyst interests you, check out sebh24’s career guide: How to become a cybersecurity analyst in 2023: the ultimate guide.
Recommended read: What is a SOC analyst? Skills & career path Q&A (with a seasoned blue teamer).
Cybersecurity engineer
A cybersecurity engineer is engaged in constructing and reinforcing an organization's security architecture. Their key responsibilities involve:
-
Designing secure solutions: Tailoring specific security measures to the organization's needs.
-
Implementing and maintaining security tools: Deploying the latest tools and technologies to fortify defenses.
-
Compliance management: Ensuring alignment with regulatory requirements and industry best practices.
Can you do both?
Yes! It’s common for a cybersecurity analyst to perform the core responsibilities of a cybersecurity engineer and vice versa. Due to the cybersecurity skills gap, many security professionals must wear multiple hats to protect their organizations.
If you're intrigued by both of these roles, exploring these hybrid positions could be your pathway to a fulfilling and dynamic career; you can pair your detection and monitoring know-how with your creative engineering and tool development skills!
How to become a cybersecurity engineer
Becoming a cybersecurity engineer involves challenges, discoveries, and personal growth. The roadmap isn't etched in stone, but here's one of the infinite paths you can take to get you to your destination.
Step #1: Gain the foundational skills
Being able to step back and learn how to visualize a problem and fit pieces of the puzzle together to create a solution is a must-have skill in security engineering.
This ability stems from developing fundamental defensive cybersecurity skills. A strong networking background, deep knowledge of the OSI layers, and recognition of normal vs. malicious network traffic are vital. (I use my networking skills to integrate our environment's tools, such as SIEM, SOAR, EDR/XDR, and firewalls.)
-
Gain fundamental skills: Complete fundamental and easy defensive modules such as the Introduction to Networking and JavaScript Deobfuscation on HTB Academy.
-
Earn entry-level certifications: Certifications like CompTIA's Network+, Security+, and HTB’s CDSA signify your commitment and build your credibility and can help land you entry-level positions.
-
Join the community: Engage with like-minded professionals and enthusiasts in online communities like Discord servers and forums. Learning from others' experiences can be invaluable.
Step #2: Level up your skills
-
Expand fundamental skills: Dive deeper with intermediate to advanced training by completing medium and hard defensive HTB academy modules such as Windows Attacks & Defense and Secure Coding 101: JavaScript.
-
Pursue intermediate-level certifications: Bridge the gap between entry-level and higher-level certifications with mid-level certifications such as the Cisco Certified Network Associate (CCNA), CompTIA’s Cybersecurity Analyst (CySA+), and blue team-focused Global Information Assurance Certifications (GIAC).
Note💡: Our SOC analyst certification (CDSA) is entry-level but provides an intermediate level of job proficiency once completed. This means you can start it as a beginner and develop market-place-ready skills to prepare you for real jobs.
-
Pursue higher-level certifications: Look for advanced certifications like CompTIA's CASP+ (soon to be called SecurityX), Certified Information Systems Security Professional (CISSP), Certified Information SecurHapity Manager (CISM), and Cisco Certified Network Professional (CCNP) – Security.
-
Build home labs: Create simulated environments mimicking production networks. Experimentation in a safe space fosters creativity and understanding. Your home lab allows you to learn from mistakes without the consequences of bringing down production networks.
-
Expand soft skills: Your technical skills aren't enough; people skills are also essential. It's not about being extroverted but being someone others enjoy working with. As you reach higher levels of technical expertise, make time to enhance your soft skills. A good starting point might be a book like "How to Win Friends and Influence People" by Dale Carnegie.
Step #3: Market yourself and build your network
-
Share your knowledge: Start a blog, YouTube channel, or use other platforms to showcase your insights, projects, and skills. Be it through tutorials or simply documenting what you are learning, let the world see your expertise!
-
Contribute to the field: Engage in open-source projects or publish articles that add value to the cybersecurity community.
-
Mentor and assist beginners: Guiding newcomers enhances your understanding and builds a supportive community.
-
Craft a portfolio: Document your achievements, certifications, and notable projects.
-
Network actively: Connect with cybersecurity professionals on LinkedIn, attend conferences, participate in events, and join Discord servers. Building professional relationships can unlock unexpected opportunities.
Ingenuity, innovation, and automation set security engineers apart; it's about doing what you can with what you have. If you can do something or create something that saves your business money, time, or risk, I guarantee you will be loved."
Matt Russo, Cyber Security Systems Engineer, Sargento Foods Inc, 2023
Step #4: Start applying
-
Tailor your resume: Align your resume with the specific roles you're targeting. Highlight relevant skills and experiences.
-
Leverage your network: Reach out to connections who might help in your job search. Personal referrals can make a significant difference.
-
Prepare for interviews: Research common interview questions and practice articulating your experiences and approach to problem-solving. Your hands-on skills should be at the forefront of your interviews.
-
Show enthusiasm for continuous learning: The cybersecurity field is ever-evolving. Express your commitment to staying on top of new developments and technologies. Employers want to see passion for the field from job candidates.
Becoming a cybersecurity engineer isn't a leap but a series of deliberate and well-calibrated steps. With each phase, you build a more holistic understanding of the cyber landscape.
9 Important skills for cybersecurity engineers

-
Malware analysis: Cybersecurity engineers must understand the behavior and intentions behind malicious code to counteract threats preemptively. This knowledge helps in identifying vulnerabilities and creating more secure systems. You can develop this skill through the HTB Academy's Introduction to Malware Analysis module, which offers hands-on exercises.
-
Threat hunting: Proactively detecting threats before they cause harm is vital for maintaining security. This approach requires a thorough understanding of potential vulnerabilities and constant vigilance. The Introduction to Threat Hunting & Hunting with Elastic Academy module is a great starting point for honing this skill.
-
Understanding Windows event logs: Identifying hidden threats within system logs provides valuable insights into ongoing or past security incidents. This analysis helps in threat mitigation and prevention. You can dive deeper into this area with HTB Academy's Windows Event Logs & Finding Evil module.
-
Log analysis: Analyzing logs using tools like Splunk assists in uncovering patterns and signs of breaches. This knowledge is essential for timely response and system integrity. The Understanding Log Sources & Investigating with Splunk module in the HTB Academy offers a practical learning experience.
-
Programming and scripting: A basic familiarity with programming, particularly with languages like Python, PowerShell, and Bash, is indispensable for a cybersecurity engineer. Crafting custom scripts and understanding how various code works allows for creating unique security solutions and automating repetitive tasks. (Read my guide on the 7 best programming languages for cybersecurity to learn more.)
-
Network security: Cybersecurity engineers must protect and maintain secure networks. This involves understanding firewall rules, network protocols, and potential entry points for attackers. Hands-on practice with network simulations and real-world scenarios can build this skill.
-
Incident response: Responding effectively to security incidents minimizes potential damage and helps understand how the breach occurred. Practical experience in simulated cyber attack environments will sharpen this skill.
-
Compliance and risk management: Ensuring alignment with regulations and understanding the risks associated with different business operations is paramount. Keeping up with industry guidelines and learning about security frameworks like the NIST CFM will provide a solid foundation.
Types of cybersecurity engineer
Cybersecurity engineering is no longer a monolithic field. It has branched into several specialized areas, each focusing on specific aspects of security. Understanding these sub-sections can guide aspiring engineers to find their niche:
-
Network security engineer: The position primarily revolves around ensuring the protection and reliability of an organization's network. Key responsibilities involve setting up firewalls, configuring security devices, and monitoring network traffic to identify suspicious activities.
-
Application security engineer: With the rise of software development, securing applications against breaches is paramount. Application security engineers work closely with developers to integrate security within the code, employing tools and methodologies that minimize vulnerabilities.
-
Cloud security engineer: As businesses migrate to cloud platforms, the need for security in these environments grows. These engineers specialize in securing cloud infrastructure and services, ensuring that data is protected and compliant with relevant regulations.
-
Incident response (IR) engineer: This type of engineer is on the front lines of dealing with security breaches. They focus on rapid identification, investigation, and remediation of incidents, working closely with various teams to restore normal operations.
-
Security automation engineer: Emphasizing efficiency, this role involves automating security tasks and processes. Utilizing tools like Python and shell scripting, they create scalable solutions enabling quicker responses to threats and freeing human resources for more complex challenges.
-
Compliance and risk management (RM) engineer: This role ensures that security measures adhere to regulatory standards and policies. These engineers assess risks and align security practices with legal requirements, facilitating smooth audits and maintaining organizational trust.
-
Industrial/operational technology (OT) security engineer: Focusing on critical infrastructure, such as energy grids, water treatment plants, and manufacturing facilities, these engineers OT systems that are increasingly connected to digital networks. Their work helps prevent potentially catastrophic disruptions.
-
Embedded security engineer: Securing embedded systems is essential in Internet of Things (IoT) devices. These engineers work on hardware-level security, protecting devices from medical equipment to smart home gadgets.
These diverse roles show the breadth of opportunities available for security engineers! It’s a great career path for finding and aligning with a specialty that suits your interests and skills.
What if you don't have an IT background or degree?
My good friend Matt Russo is proof that you don't need a degree to become a cybersecurity engineer. He served with me as an Active Duty U.S. Air Force client systems technician (system administrator) in South Korea from 2019-2020.
Although armed with almost six years of enterprise IT experience, Matt embarked on his cybersecurity journey with small amounts of real-world exposure to cybersecurity. He doesn't have a college degree at the time of writing and has become a successful cybersecurity engineer.
My journey began at the help desk, a crucial stepping stone that shaped my troubleshooting skills. Now, as a security engineer, I am almost always working on projects or being tasked with something I have little to no exposure to.
If you are a resourceful and inventive person who can think independently, this is a job for you.
Matt Russo, Cyber Security Systems Engineer, Sargento Foods Inc, 2023
Unfortunately, many cybersecurity engineer roles aren't entry-level, requiring at least a couple of years of IT experience.
I'm sharing this not to discourage you but to be honest and transparent. I want you to succeed, but you likely won't start as a cybersecurity engineer without prior experience. It's not impossible, but it's definitely not the industry norm right now.
The good news is that you can pivot from any IT background into a cybersecurity engineer position as long as you diligently work on your skill set. For this reason, I advise pursuing entry-level IT/cybersecurity positions as you build toward the cybersecurity engineer skill level.
Remember, paid experience often matters more than training, certifications, and degrees combined. So seize the first paid opportunity you can find!
Here's more encouraging news: a college degree isn't a must-have. Even if a job posting mentions a degree, consider it a "nice to have," not a requirement.
While a degree might give you an edge among applicants, don't be deterred if you lack one. Your unique skills and experience can still make you a standout candidate in any cybersecurity role.
Build your defensive security skills
|
Author bio: Kyser Clark (KyserClark), Cyber Defense Operations (1D771), United States Air Force (Active duty) Kyser is a Cyber Defense Operations leader with over five years of active duty U.S. Air Force experience specializing in offensive security, ethical hacking, penetration testing, and red teaming. His credentials include a Bachelor of Science (BS) in Cybersecurity Management & Policy from the University of Maryland Global Campus (UMGC), and 11 industry certifications: OffSec Certified Professional (OSCP), (ISC)² Certified Information Systems Security Professional (CISSP), eLearnSecurity Junior Penetration Tester (eJPT), EC-Council Certified Ethical Hacker (CEH), Cisco Certified Network Associate (CCNA), CompTIA PenTest+, Cybersecurity Analyst (CySA+), Cloud+, Linux+, Security+, and Network+. Kyser encourages you to connect with him in these places in cyberspace: |







